The framework core provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand. It can also be used when your organization needs to benchmark its current security operations.
You Choose A Cybersecurity Framework For Your Financial Organization, They act as the backbone of the framework core that all other elements are organized around. This function helps the organization identify the existing cyber touch points within a business environment.

The nist cybersecurity framework is voluntary guidance, based on existing standards, guidelines, and practices to help organizations better manage and reduce cybersecurity risk. A cybersecurity framework can be a vital guidepost. This can include executing and maintaining response processes and procedures, coordinating with internal and external stakeholders, conducting analysis to ensure. This function helps the organization identify the existing cyber touch points within a business environment.

Why Cyber Risk Prioritization is Essential to a Solid TPRM Program It is designed to test the skills and knowledge presented in the course. Five main processes that define the cybersecurity framework are: The nist cybersecurity framework is voluntary guidance, based on existing standards, guidelines, and practices to help organizations better manage and reduce cybersecurity risk. Which framework are you choosing? Used by 32% of organizations, the cis critical security controls.

New NIST Framework Strengthens Risk Management Netgain Using the nist cybersecurity framework is a great way to standardize your cybersecurity and risk management. The framework’s respond function provides guidance on how to develop and implement appropriate actions in response to a detected cybersecurity event to effectively contain its impact. There are multiple task types that may be available in this quiz. The framework implementation tiers assist. Organizations.

Cyber Security Responsibility 5 Areas of Investment Learning Tree It is designed to test the skills and knowledge presented in the course. The framework implementation tiers assist. The recommendations of the iso 27000 cybersecurity model is broken down into the following areas for security managers to use best practices to reach program maturity: Using the nist cyber security framework can be a tool to verify your processes and give.

NIST CSF Gap Analysis Assessment Kyber Security The framework implementation tiers assist. Understanding the similarities and differences across the top 25 security frameworks can help you create a more robust cybersecurity compliance program. It is designed to test the skills and knowledge presented in the course. Five main processes that define the cybersecurity framework are: You choose a cybersecurity framework for your financial organization that implements an.

7 Cybersecurity Frameworks To Reduce Cyber Risk Used by 32% of organizations, the cis critical security controls are a set of 20 actions designed to mitigate the threat of the majority of common cyber attacks. A cybersecurity policy is a summary of all the requirements your organization should meet, all the practices you intend to implement, and the tools that can be used for doing so. The.

The Financial Industry Cyber Security Laggards Risk Management Monitor A cybersecurity policy is a summary of all the requirements your organization should meet, all the practices you intend to implement, and the tools that can be used for doing so. You can put the nist cybersecurity framework to work in your business in these five areas: A cybersecurity framework is, essentially, a system of standards, guidelines, and best practices.

Cyber Security Strategy ACQUI Technology in Long Beach CA This function helps the organization identify the existing cyber touch points within a business environment. A cybersecurity policy is a summary of all the requirements your organization should meet, all the practices you intend to implement, and the tools that can be used for doing so. Five main processes that define the cybersecurity framework are: A cyber security framework acts.

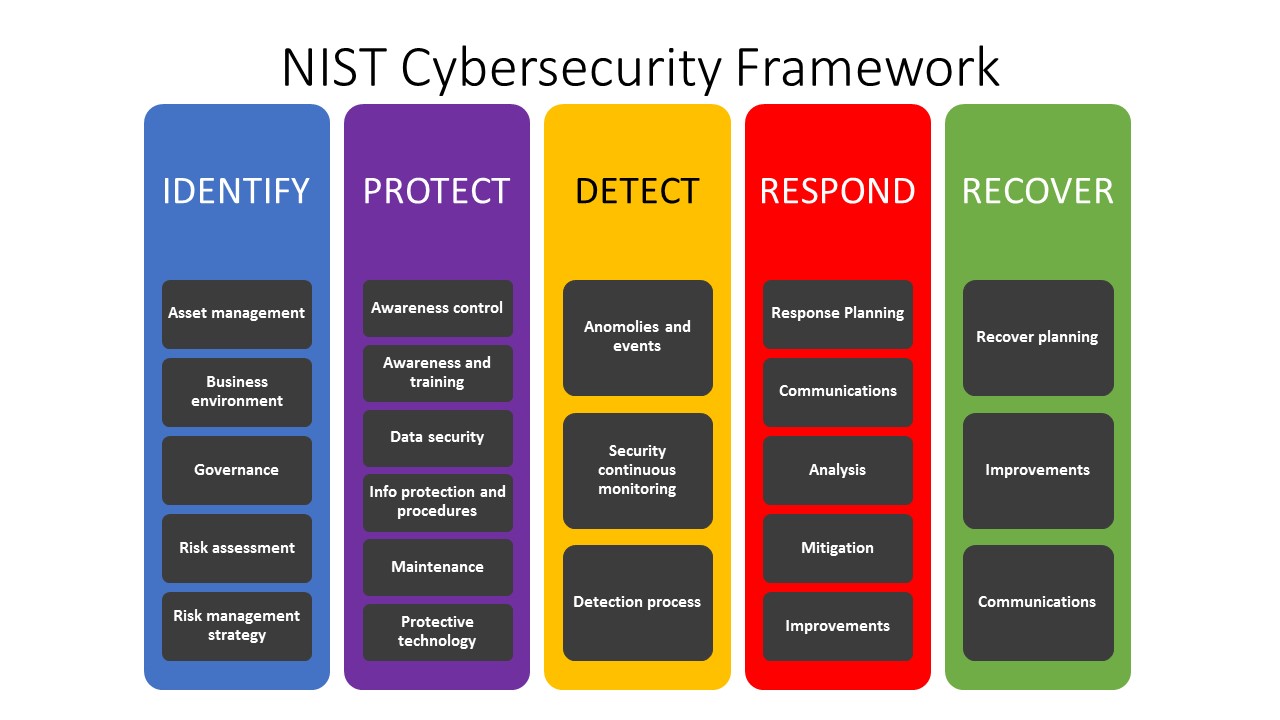
Types of Testing What�s Right for Your Business You can put the nist cybersecurity framework to work in your business in these five areas: Identify, protect, detect, respond, and recover. The nist cybersecurity framework is voluntary guidance, based on existing standards, guidelines, and practices to help organizations better manage and reduce cybersecurity risk. The principal purpose of the security framework is to reduce the likelihood. Having a written.

Cybersecurity Visualization Techniques to Gain Executive BuyIn The cybersecurity framework consists of three main components: This function helps the organization identify the existing cyber touch points within a business environment. A cyber security framework acts as a roadmap for organizing cybersecurity risk management efforts. Identify, protect, detect, respond, and recover. There are multiple task types that may be available in this quiz.

The scope of a cybersecurity assessment and how it can help your Building a hybrid security framework. They typically match security objectives, like avoiding unauthorized system access with controls like requiring a. Used by 32% of organizations, the cis critical security controls are a set of 20 actions designed to mitigate the threat of the majority of common cyber attacks. The cybersecurity framework consists of three main components: The controls were designed.

NIST CSF Cyber Oak Solutions Asd’s essential 8 takes a maturity model approach to cybersecurity, listing three levels. Australian signals directorate (asd) essential 8. You can put the nist cybersecurity framework to work in your business in these five areas: There are multiple task types that may be available in this quiz. Identity, protect, detect, respond, and recover.

9 Ways to Protect Your Business from Cyber Attacks PrivacyEnd With a framework as your guidepost, you’ll gain vital insight into where your highest security risk is. Ensuring the cyber security framework receives wide adoption across your organization and suitable funding is one way to do this. This function helps the organization identify the existing cyber touch points within a business environment. Australian signals directorate (asd) essential 8. Which framework.

Defining a Security Strategy WHY A cybersecurity framework is, essentially, a system of standards, guidelines, and best practices to manage risks that arise in the digital world. The recommendations of the iso 27000 cybersecurity model is broken down into the following areas for security managers to use best practices to reach program maturity: The framework is intended to provide security managers with a dependable, methodical.

Assessing Microsoft 365 security solutions using the NIST Cybersecurity A cybersecurity policy is a summary of all the requirements your organization should meet, all the practices you intend to implement, and the tools that can be used for doing so. The framework implementation tiers assist. The framework is meant to complement your organization’s cyber security program, not replace it. Organizations can also leverage a hybrid framework by choosing specific.

Part II Implementing Your Cybersecurity Program Edwards Performance This can include executing and maintaining response processes and procedures, coordinating with internal and external stakeholders, conducting analysis to ensure. You choose a cybersecurity framework for your financial organization that implements an effective and auditable set of governance and management processes for it. Having a written cybersecurity policy in place makes it easier for an organization to establish an effective.

SC Cybersecurity Any cybersecurity framework will work based upon this process. Used by 32% of organizations, the cis critical security controls are a set of 20 actions designed to mitigate the threat of the majority of common cyber attacks. Identity, protect, detect, respond, and recover. The framework is meant to complement your organization’s cyber security program, not replace it. The recommendations of.

What’s Covered Under Cyber Risk Insurance Understanding the similarities and differences across the top 25 security frameworks can help you create a more robust cybersecurity compliance program. Building a hybrid security framework. Create and share a company cybersecurity policy that covers: This function helps the organization identify the existing cyber touch points within a business environment. Your it security management framework will effectively explain to all.
Top 12 Ways Small To Med Businesses Can Reduce Cyber Risk Abstract A cheat sheet for professionals (free pdf) (techrepublic) president barack obama recognized the cyber threat in 2013, which led to his cybersecurity executive. This can include executing and maintaining response processes and procedures, coordinating with internal and external stakeholders, conducting analysis to ensure. They typically match security objectives, like avoiding unauthorized system access with controls like requiring a. Building a.

How to get started with the NIST Cybersecurity Framework (CSF) Expel Used by 32% of organizations, the cis critical security controls are a set of 20 actions designed to mitigate the threat of the majority of common cyber attacks. You can put the nist cybersecurity framework to work in your business in these five areas: The principal purpose of the security framework is to reduce the likelihood. A cheat sheet for.

How Vulnerable Are You To a Cyber Attack? A SelfAssessment Tool for Used by 32% of organizations, the cis critical security controls are a set of 20 actions designed to mitigate the threat of the majority of common cyber attacks. With a framework as your guidepost, you’ll gain vital insight into where your highest security risk is. There are multiple task types that may be available in this quiz. Having a written.

Cyber Security Certification SelfPaced Courses Savannah Technical National institute of standards & technology (nist) recently released version 1.1 of the cybersecurity framework, and the security industry response is stronger than ever. Used by 32% of organizations, the cis critical security controls are a set of 20 actions designed to mitigate the threat of the majority of common cyber attacks. It can also be used when your organization.

Information Security Compliance Which regulations apply? Having a written cybersecurity policy in place makes it easier for an organization to establish an effective cybersecurity routine and maintain a certain level of data security in the long term. These five functions were selected because they represent the five primary. The five functions included in the framework core are: With a framework as your guidepost, you’ll gain vital.

How financial services organizations can manage cyber risk EY Global Australian signals directorate (asd) essential 8. You choose a cybersecurity framework for your financial organization that implements an effective and auditable set of governance and management processes for it. This function helps the organization identify the existing cyber touch points within a business environment. This can include executing and maintaining response processes and procedures, coordinating with internal and external stakeholders,.

The Best Cybersecurity Training Programs for Your Employees USA TODAY The controls were designed by a group of volunteer experts from a range of fields, including cyber analysts, consultants, academics, and auditors. It is designed to test the skills and knowledge presented in the course. It can also be used when your organization needs to benchmark its current security operations. These five functions were selected because they represent the five.

Cyber Basics Understand Vulnerabilities, Threats & Exploits These five functions were selected because they represent the five primary. Using the nist cyber security framework can be a tool to verify your processes and give your insurance carrier more confidence that you’re making good choices in your data protection. Board subcommittee reporting when rolling out a cyber security framework, it is important to establish an ongoing feedback loop.
With a framework as your guidepost, you’ll gain vital insight into where your highest security risk is. Cyber Basics Understand Vulnerabilities, Threats & Exploits.
A cybersecurity policy is a summary of all the requirements your organization should meet, all the practices you intend to implement, and the tools that can be used for doing so. Organizations can also leverage a hybrid framework by choosing specific controls from other frameworks to meet their compliance requirements and business needs. National institute of standards & technology (nist) recently released version 1.1 of the cybersecurity framework, and the security industry response is stronger than ever. Ensuring the cyber security framework receives wide adoption across your organization and suitable funding is one way to do this. Your it security management framework will effectively explain to all parties (internal and external) how information, systems, and services are managed within your organization to ward off hackers. The framework is intended to provide security managers with a dependable, methodical method of mitigating cyber risk, regardless of how complicated the environment may be.
Ensuring the cyber security framework receives wide adoption across your organization and suitable funding is one way to do this. Australian signals directorate (asd) essential 8. The cybersecurity framework consists of three main components: Cyber Basics Understand Vulnerabilities, Threats & Exploits, Identity, protect, detect, respond, and recover.







