Preparing the ground for attack. Answers will vary depending on current events.
Three Examples Of Social Engineering, Due to a social engineering and bec scam, cabarrus county, in the united states, suffered a loss of usd 1.7 million in 2018. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious.

Social engineering is something that we’ve all done, whether we’ve realised it or not. Lewis morgan 17th may 2018. One of the most famous social engineering attacks took place sometime around 1200 b.c. It is also known as emotional manipulation.

Hackers find successful cyber target Humans SiouxFalls.Business Deciding what attack method (s) to use. As one of the most popular social engineering attack types, phishing scams are email and text message campaigns aimed at creating a sense of urgency, curiosity or fear in victims. This form of social engineering plays off a trust we have in our phones and in voices that we don’t have for emails..

Democracy 3 Social Engineering on Steam If you feel someone is leveraging social engineering, press the person and ask for their name, email address, job title, etc. It then prods them into revealing sensitive information, clicking on links to malicious websites, or opening attachments that contain malware. Let�s explore the six common types of social engineering attacks: Phishing is a social engineering technique in which an.
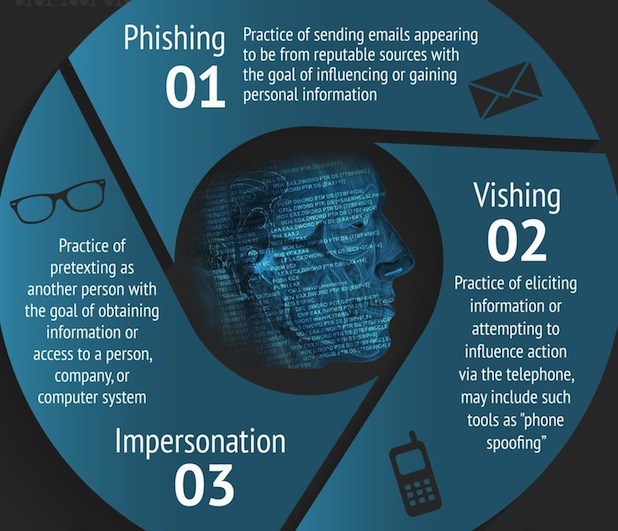
The Social Engineering Infographic Security Through Education Due to a social engineering and bec scam, cabarrus county, in the united states, suffered a loss of usd 1.7 million in 2018. Summarize three examples found in your research. If the recipient clicks on the link in the email, they will be. Preparing the ground for attack. This scenario focuses on your behavior (hopefully, this won�t be too uncomfortable).

Understanding Social Engineering Techniques Using malicious emails, hackers impersonated county suppliers and requested payments to a new bank account. This lab requires the research of social engineering and the identification of ways to recognize and prevent it. One of the most famous social engineering attacks took place sometime around 1200 b.c. A threat actor mostly follows the steps below: Phishing scams and smishing (fake.

Sustainability Free FullText The Cognitive Framework of the Email fraud is particularly dangerous because these socially engineered attacks are hard to detect with conventional cyberattacks. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious. This form of social.

PPT Engineering as Social Experimentation PowerPoint Presentation Deciding what attack method (s) to use. Lewis morgan 17th may 2018. For example, “ paypal has closed your account as it has been hacked; If you feel someone is leveraging social engineering, press the person and ask for their name, email address, job title, etc. The email will attempt to get the user to click a link or download.

Venn Diagrams Solution He managed to trick the trojans into believing that the greek. This scenario focuses on your behavior (hopefully, this won�t be too uncomfortable). Influencing is another important social engineering art of things which affect to others (victims). Summarize three examples found in your research. Such an attacker can gain physical access to restricted areas, thus providing further opportunities for attacks.

Module 3 social engineeringb Phishing is the most common type of. Email fraud is particularly dangerous because these socially engineered attacks are hard to detect with conventional cyberattacks. Social engineering is the art of manipulating people so they give up confidential information. When ulysses, the commander of the greek army, concocted the famous trojan horse scam. One of the most famous social engineering attacks.

The Environmental, Economic, and Social Components of Sustainability This done in a number of ways including: The email will attempt to get the user to click a link or download an attachment using tricks like concern and urgency. This form of social engineering plays off a trust we have in our phones and in voices that we don’t have for emails. If the recipient clicks on the link.

Case Study 3 Social Engineering (Security) Phishing Social engineering is something that we’ve all done, whether we’ve realised it or not. For example, instead of trying to find a software vulnerability, a social engineer might call an employee and pose as an it support person, trying to trick the employee into divulging his password. For most social engineering attacks, the first step is to collect information about.

Social engineering 3 examples of human hacking CSO Online How is social engineering functioning? Obviously, it’s when an attacker presents himself or his communication as originating from another party. Phishing is the most common type of. One of the most famous social engineering attacks took place sometime around 1200 b.c. Similar tactics or used in smishing or sms phishing.

» The 3 Main Types of Social Engineering Attacks (Infographic) This form of social engineering plays off a trust we have in our phones and in voices that we don’t have for emails. Here are some examples of social engineering attacks used repeatedly by attackers to gain access and benefits in terms of finance, access point, etc., or commit the different types of a cyber attack. Due to a social.

What is Social Engineering? Techniques, Examples and Prevention Tips The email will attempt to get the user to click a link or download an attachment using tricks like concern and urgency. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install.

Albert Bandura�s Theory of SelfEfficacy Video & Lesson Transcript It then prods them into revealing sensitive information, clicking on links to malicious websites, or opening attachments that contain malware. This scenario focuses on your behavior (hopefully, this won�t be too uncomfortable). Deciding what attack method (s) to use. Here are some examples of social engineering attacks used repeatedly by attackers to gain access and benefits in terms of finance,.

1.2.1.3 Social Engineering Principles (Reasons for Effectiveness For example, a social engineer might send an email that appears to come from a customer success manager at your bank. Influencing is another important social engineering art of things which affect to others (victims). Obviously, it’s when an attacker presents himself or his communication as originating from another party. Summarize three examples found in your research. Due to a.

Top 5 Phishing Red Flags (Infographic) Social engineering influences to the victims using various tactics and then, gains the victim’s trust and get unauthorized access of sensitive information and resources. Social engineering is something that we’ve all done, whether we’ve realised it or not. The email will attempt to get the user to click a link or download an attachment using tricks like concern and urgency..

Module 3 social engineeringb For example, a social engineer might send an email that appears to come from a customer success manager at your bank. The medium can be email, web, phone, usb drives, or some other thing. When ulysses, the commander of the greek army, concocted the famous trojan horse scam. This form of social engineering plays off a trust we have in.

3.5.7 Lab Social Engineering MMuniz.docx Lab Social Engineering How is social engineering functioning? The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious. And they’ll likely abandon the pursuit. Instead, social engineering preys on human emotion to bypass security.

Phishing awareness презентация онлайн Social engineering influences to the victims using various tactics and then, gains the victim’s trust and get unauthorized access of sensitive information and resources. This form of social engineering plays off a trust we have in our phones and in voices that we don’t have for emails. For example, a social engineer might send an email that appears to come.

Social Constructivism, Technological Determinism, Technological Momen… When ulysses, the commander of the greek army, concocted the famous trojan horse scam. In each example, social engineering scammers are looking for the right target and the right emotional trigger. Summarize three examples found in your research. This form of social engineering plays off a trust we have in our phones and in voices that we don’t have for.
![Why You Should Be Afraid of CEO Fraud [INFOGRAPHIC] Why You Should Be Afraid of CEO Fraud [INFOGRAPHIC]](https://i2.wp.com/cdn2.hubspot.net/hubfs/241394/CEOFraudXL.png)
Why You Should Be Afraid of CEO Fraud [INFOGRAPHIC] For example, a social engineer might send an email that appears to come from a customer success manager at your bank. Answers will vary depending on current events. Email fraud is particularly dangerous because these socially engineered attacks are hard to detect with conventional cyberattacks. When ulysses, the commander of the greek army, concocted the famous trojan horse scam. In.

Social Engineering Infographic Pindrop If you feel someone is leveraging social engineering, press the person and ask for their name, email address, job title, etc. Such an attacker can gain physical access to restricted areas, thus providing further opportunities for attacks. The email will attempt to get the user to click a link or download an attachment using tricks like concern and urgency. As.

Module 3 social engineeringb This scenario focuses on your behavior (hopefully, this won�t be too uncomfortable). Instead, social engineering preys on human emotion to bypass security and gain valuable information. One of the most famous social engineering attacks took place sometime around 1200 b.c. For most social engineering attacks, the first step is to collect information about the target. Social engineering is something that.

Electrical Engineering Capstone Project Ideas by Capstone Project Ideas If the recipient clicks on the link in the email, they will be. And they’ll likely abandon the pursuit. Preparing the ground for attack. Social engineering attacks usually happen in one or more steps. Lewis morgan 17th may 2018.

our professor at collage using the hunter2 meme as an example for The email will attempt to get the user to click a link or download an attachment using tricks like concern and urgency. It is also known as emotional manipulation. Phishing scams and smishing (fake sms/text messages) are trick users online and over the phone into giving up sensitive information or money. In each example, social engineering scammers are looking for.
This form of social engineering plays off a trust we have in our phones and in voices that we don’t have for emails. our professor at collage using the hunter2 meme as an example for.
Social engineering influences to the victims using various tactics and then, gains the victim’s trust and get unauthorized access of sensitive information and resources. Here are some examples of social engineering attacks used repeatedly by attackers to gain access and benefits in terms of finance, access point, etc., or commit the different types of a cyber attack. Email fraud is particularly dangerous because these socially engineered attacks are hard to detect with conventional cyberattacks. Such an attacker can gain physical access to restricted areas, thus providing further opportunities for attacks. How is social engineering functioning? Let�s explore the six common types of social engineering attacks:
Due to a social engineering and bec scam, cabarrus county, in the united states, suffered a loss of usd 1.7 million in 2018. Summarize three examples found in your research. Social engineering is the art of manipulating people so they give up confidential information. our professor at collage using the hunter2 meme as an example for, One of the most famous social engineering attacks took place sometime around 1200 b.c.







