Encrypting data and securing hardware. Masters of disguise and manipulation, these threats constantly evolve to find new ways to annoy, steal and harm.
Strategies To Curb Computer Security Threats And Attacks, If the security analyst decides to go down the forensic analysis path, here are five ways to fight back. Unfortunately, some companies don’t know where to start when it comes to addressing the common it security threats that exist.

It enables businesses to prepare for the inevitable, respond to emerging threats, and recover quickly from an attack. Looking out for red flags. To combat cyberthreats, microsoft amalgamates trillions of daily signals, across all clouds and all platforms, for a holistic view of the global security ecosystem. Sounds simple, identify then mitigate security risks in order of most likely to least likely, using a traditional weighted scoring method of “likelihood multiplied by potential impact.” we try to learn from others’ mistakes and misfortunes, as well as thought leaders in the industry

Cyber Proof Tips Security solutions, Computer security, Cyber attack Conduct a risk assessment to determine vulnerabilities. Computer security threats are relentlessly inventive. Let us now look at the six strategies that microsoft employs to help our customers deal with the alert fatigue problem: Examine key components of frequently used apps; Keep staff up to date on new cyber attack.

Cyber Threats Infographic Evolution and Prevention Euriun Technologies Keeping systems up to date by applying the latest patches to computers, servers, and hardware. With 24/7 threat hunting and intelligence. Basic education will not suffice to fight cybercriminals. Looking out for red flags. The entire strategy can be divided into three main parts:

Cyber Security Risks for Small Business Infographic — Vanasek Insurance Ad a fully iso 27001 certified process to help you mitigate threats. Having an incident response plan and practicing it. Unfortunately, some companies don’t know where to start when it comes to addressing the common it security threats that exist. The australian cyber security centre (acsc) has developed prioritised mitigation strategies to help cyber security professionals in all organisations mitigate.

Tips To Protect Your Business From Cyber Attacks Mitigation strategies to recover data and system availability. Control the scope of damage. Automation is necessary because threat actors study patches and create exploits, often soon after a patch is released. There are several ways to prevent these attacks. Apply all available software updates, automate the process to the extent possible, and use an update service provided directly from the.

Types of Password Attacks It enables businesses to prepare for the inevitable, respond to emerging threats, and recover quickly from an attack. Mitigation strategies to recover data and system availability. The entire strategy can be divided into three main parts: Effect of government action on threats to cybersecurity. These patches often contain essential security updates that plug known vulnerabilities.
EMSS Cyber security guidance for business Very helpful information Ad a fully iso 27001 certified process to help you mitigate threats. Implement a comprehensive backup system. Attackers are using more complicated with time. This guidance addresses targeted cyber intrusions (i.e. Effect of government action on threats to cybersecurity.

Safety from Cyber Attacks Steps that can reduce cyber threats Sprotechs Begin your cyber attack prevention strategy with the basics: To design and implement a secure cyberspace, some stringent strategies have been put in place. It staff needs to put a continuing education program in place that accomplishes two objectives: Keep staff up to date on new cyber attack. Arm yourself with information and resources to safeguard against complex and growing.

Pin by Dan Williams on Cyber Security Cybersecurity awareness, Cyber Attackers are using more complicated with time. Control the scope of damage. Control access to your systems To combat cyberthreats, microsoft amalgamates trillions of daily signals, across all clouds and all platforms, for a holistic view of the global security ecosystem. Implement a comprehensive backup system.

Top 5 Harmful Cyber Threat Types Logsign With 24/7 threat hunting and intelligence. With 24/7 threat hunting and intelligence. Keep staff up to date on new cyber attack. There should be daily backups of important new/changed data, software and configuration settings, to ensure that information can be accessed again following a cyber security incident (e.g. Protect all devices with a complicated password, share that password with the.

Active Cyber Defence infographic Cyber attack, Cyber threat, Cyber Keeping systems up to date by applying the latest patches to computers, servers, and hardware. Effect of government action on threats to cybersecurity. In general, you can safely employ. Key protections against security threats. It’s highly regarded throughout the security industry.

10 Computer Security Tips Computer security, Security tips, Malware Unfortunately, some companies don’t know where to start when it comes to addressing the common it security threats that exist. In the event of a disaster (often a cyber attack) you must have your data backed up to avoid serious downtime, loss of data and serious financial loss. Keep staff up to date on new cyber attack. Sounds simple, identify.

Combating seven common threat techniques in 2018 IT Security Guru Ad a fully iso 27001 certified process to help you mitigate threats. Basic education will not suffice to fight cybercriminals. If the security analyst decides to go down the forensic analysis path, here are five ways to fight back. The australian cyber security centre (acsc) has developed prioritised mitigation strategies to help cyber security professionals in all organisations mitigate cyber.

Cyberattacks, threats, and ransom School safety goes beyond the End of support for microsoft windows 10 under microsoft’s current servicing model, support for microsoft windows 10 will end between 18 to 30 months after release depending on the version and edition being used. Key protections against security threats. With 24/7 threat hunting and intelligence. Keeping systems up to date by applying the latest patches to computers, servers, and hardware..

What is Cyber Security? Definition, History & Importance Science and Encrypting data and securing hardware. Ad a fully iso 27001 certified process to help you mitigate threats. Web content filters are useful tools, since they can be set to block pornography, competitors� websites and hacker tool repositories, all of which figure prominently in common insider security threats. It enables businesses to prepare for the inevitable, respond to emerging threats, and.

5 NeedToKnow Cybersecurity Statistics for 2019 There are several ways to prevent these attacks. Control access to your systems The list below highlights a few methods that you can employ to keep such information security threats at bay. Avoiding disclosing sensitive information over the phone. To combat cyberthreats, microsoft amalgamates trillions of daily signals, across all clouds and all platforms, for a holistic view of the.

What is a fileless attack? How hackers invade systems without Control the scope of damage. Begin your cyber attack prevention strategy with the basics: Steps that can be taken include: The first five controls of the cis 20 are particularly important. The first step in a cybersecurity risk mitigation strategy should be to conduct a cybersecurity risk assessment, which can help uncover potential gaps in your organization’s security controls.

Is Europe ready to deal with cyber terrorism? Debating Europe Avoiding disclosing sensitive information over the phone. This chapter explains the major strategies employed to ensure cybersecurity, which include the following −. Encrypting data and securing hardware. Restricting the use of administrative privileges is one of the eight essential mitigation strategies from the strategies to mitigate cyber security incidents. Arm yourself with information and resources to safeguard against complex and.

Pin by marketing on a1 Cyber security, Cyber threat, Cybersecurity Steps that can be taken include: The entire strategy can be divided into three main parts: Multiple studies have proven them to be an effective defense against about 85% of cyberattacks, according to cis. It’s highly regarded throughout the security industry. The first step in a cybersecurity risk mitigation strategy should be to conduct a cybersecurity risk assessment, which can.

Protect Your Business from Cyber Attacks ProSec UK Security Services With 24/7 threat hunting and intelligence. These patches often contain essential security updates that plug known vulnerabilities. Those executed by advanced persistent threats such as foreign intelligence services), ransomware and external. Restricting the use of administrative privileges is one of the eight essential mitigation strategies from the strategies to mitigate cyber security incidents. Proposed method(s) for mitigating these types of.

Pin by Kamila Ila Ila on Web design and graphic Cyber security, Ddos End of support for microsoft windows 10 under microsoft’s current servicing model, support for microsoft windows 10 will end between 18 to 30 months after release depending on the version and edition being used. Mitigation strategies to recover data and system availability. Incorporate zero trust and ssl inspection; Attackers are using more complicated with time. Let us now look at.

Pin on Cybersecurity (IT & OT) As cyber threats are evolving rapidly, your optimized security network can become outdated within no time, putting your organization at the risk of cyberattack. To design and implement a secure cyberspace, some stringent strategies have been put in place. Apply all available software updates, automate the process to the extent possible, and use an update service provided directly from the.

Infographic Cyber security threats at alltime high Times of India Conduct a risk assessment to determine vulnerabilities. The first five controls of the cis 20 are particularly important. Here are 6 top strategies for mitigating cybersecurity incidents across your it ecosystem: Mitigation strategies to recover data and system availability. The list below highlights a few methods that you can employ to keep such information security threats at bay.

How Application Security Strategy Helps fight CyberAttacks In the event of a disaster (often a cyber attack) you must have your data backed up to avoid serious downtime, loss of data and serious financial loss. If the security analyst decides to go down the forensic analysis path, here are five ways to fight back. To design and implement a secure cyberspace, some stringent strategies have been put.

Readout top articles on Industrial (ICS/OT) Cyber Security Management Mitigation strategies to recover data and system availability. Implement a comprehensive backup system. There should be daily backups of important new/changed data, software and configuration settings, to ensure that information can be accessed again following a cyber security incident (e.g. Keeping systems up to date by applying the latest patches to computers, servers, and hardware. As cyber threats are evolving.
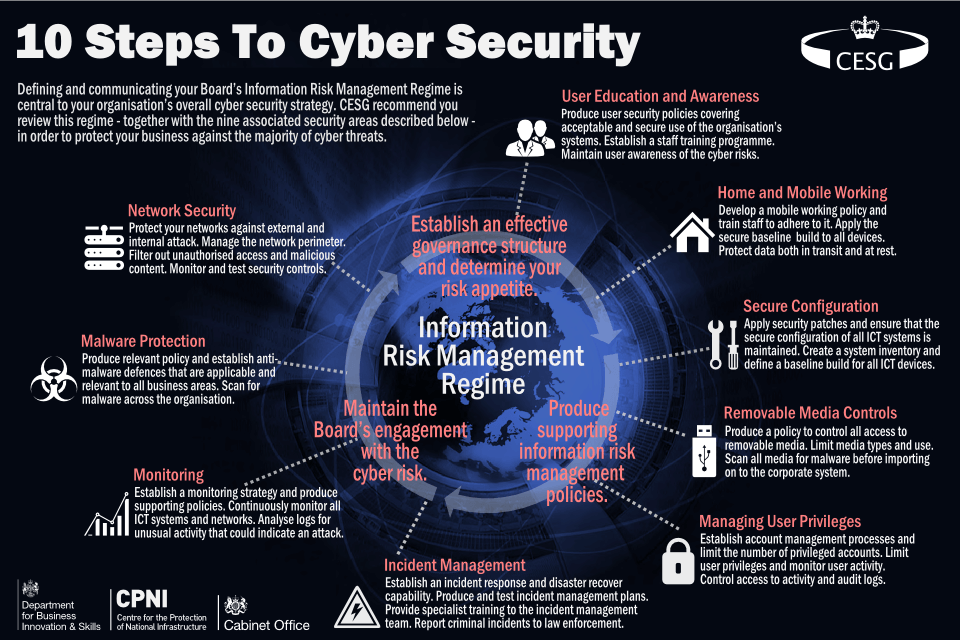
![[Withdrawn] Common Cyber Attacks Summary GOV.UK [Withdrawn] Common Cyber Attacks Summary GOV.UK](https://i2.wp.com/assets.publishing.service.gov.uk/government/uploads/system/uploads/image_data/file/35290/common_cyber_attacks.png)
[Withdrawn] Common Cyber Attacks Summary GOV.UK Looking out for red flags. Examine key components of frequently used apps; Steps that can be taken include: Those executed by advanced persistent threats such as foreign intelligence services), ransomware and external. Masters of disguise and manipulation, these threats constantly evolve to find new ways to annoy, steal and harm.
Implement a comprehensive backup system. [Withdrawn] Common Cyber Attacks Summary GOV.UK.
See how these five controls can help your organization below. Protect all devices with a complicated password, share that password with the device user only and commit it. Let us now look at the six strategies that microsoft employs to help our customers deal with the alert fatigue problem: Using the latest in machine learning. Here are 6 top strategies for mitigating cybersecurity incidents across your it ecosystem: Begin your cyber attack prevention strategy with the basics:
It staff needs to put a continuing education program in place that accomplishes two objectives: The entire strategy can be divided into three main parts: It enables businesses to prepare for the inevitable, respond to emerging threats, and recover quickly from an attack. [Withdrawn] Common Cyber Attacks Summary GOV.UK, To design and implement a secure cyberspace, some stringent strategies have been put in place.







