Examples of controls include encrypting sensitive data, maintaining a policy to patch systems regularly, and inventorying it assets. You are viewing this page in an unauthorized frame window.
Nist Cybersecurity Framework Examples, Draft nistir 8286c, staging cybersecurity risks for enterprise risk management and governance oversight, is now A notional example of types of tools, processes, or other method that could be used to help implement a task.

The nist cybersecurity framework (csf) was initially released in 2014 and last updated in 2018. To protect against cyberattacks, the cybersecurity team needs a thorough understanding of what. Examples of outcome categories within this function include: Draft nistir 8286c, staging cybersecurity risks for enterprise risk management and governance oversight, is now

NIST CSF 1.1 Excel Workbook Available Watkins Consulting The nist cybersecurity framework (nist csf) consists of standards, guidelines, and best practices that help organizations improve their management of cybersecurity risk. A breakdown of the 6 rmf steps. Nist cybersecurity framework translated into plain english(title 60). Nist framework is divided into 5 main functions. Identity, protect, detect, respond, and recover.

Understanding NIST’s Cybersecurity Framework Blog Tenable® It fosters cybersecurity risk management and related communications among both internal and external stakeholders, and for larger organizations, helps to better integrate. The nist cybersecurity framework (csf) was initially released in 2014 and last updated in 2018. The nist cybersecurity framework comprises five functions of cybersecurity activity, with a strong focus on incident response. Technology cybersecurity framework (nist csf). Controls.

What is the NIST Cybersecurity Framework? Balbix A cybersecurity framework is a list of implementable controls (both technical and process), which in totality represent a cybersecurity program. It fosters cybersecurity risk management and related communications among both internal and external stakeholders, and for larger organizations, helps to better integrate. We are excited to announce that the framework has been translated into french! This page describes reasons for.

NIST Cybersecurity Framework Guide 2021 Core, Implementation & Profile Examples include industrial control systems, building automation systems, transportation systems, physical access control systems, physical environment monitoring systems, and physical environment measurement systems. The core is “a set of activities to achieve specific cybersecurity outcomes, and references examples of guidance to achieve those. To protect against cyberattacks, the cybersecurity team needs a thorough understanding of what. Examples of controls include.
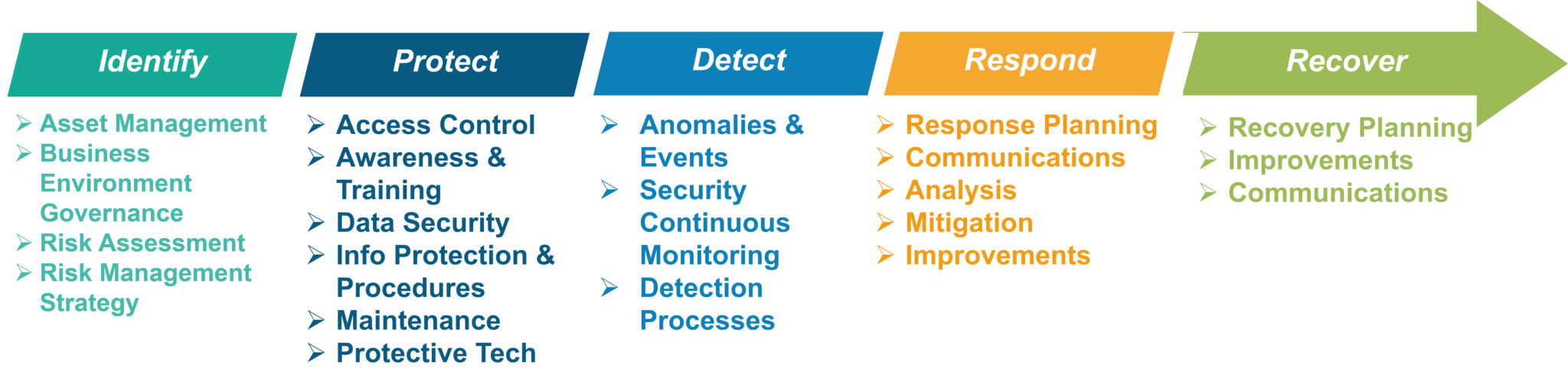
A Beginner�s Guide To Cybersecurity Framework Edureka Ensuring anomalies and events are detected, and their potential impact is understood implementing security continuous monitoring capabilities to monitor cybersecurity events and verify the effectiveness of protective measures including network and physical activities For example, in 2015, the federal financial institutions. Yet, increasingly, it is recognized as a national gold standard. Nist cybersecurity framework translated into plain english(title 60). These.

Cybersecurity Framework (Excel) NIST Spreadsheets The first function of the framework, nist defines the identify function as calling on the need to develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.” the focus is on the business and how it relates to cybersecurity risk, especially. You are viewing this page in an unauthorized frame window. For example, or retailers that.

Cyber Security Architecture with NIST Cyber Security Framework Cybersecurity framework steps for small manufacturers helps small manufacturers understand the nist cybersecurity framework and how they can use it to manage their cyber risks. In fact, some industry regulatory bodies have published additional implementation guidance supporting the framework. To protect against cyberattacks, the cybersecurity team needs a thorough understanding of what. Controls vary based on the framework. A breakdown.

Understanding NIST’s Cybersecurity Framework Blog Tenable® These controls can be classified under specific. Use nist�s framework to manage and control your cybersecurity threats and attacks. This article will explain what the nist framework is and how it is implemented. Now that you�ve seen a sample of our approach, please consider purchasing our complete product: Cybersecurity framework steps for small manufacturers helps small manufacturers understand the nist.

Implementing the NIST Cybersecurity Framework Using COBIT They support an organization in expressing its management of cybersecurity risk by addressing threats and developing by learning from past activities. The national institute of standards and technology’s (nist) cybersecurity framework, formally titled the framework for improving critical infrastructure cybersecurity, can overwhelm even experienced security professionals with its complexity. These functions are further divided into categories, which correspond to various.

Mapping the NIST Cybersecurity Framework (CSF) to the Target of Evaluation Controls vary based on the framework. It fosters cybersecurity risk management and related communications among both internal and external stakeholders, and for larger organizations, helps to better integrate. News and updates from nist�s computer security and applied cybersecurity divisions. Identity, protect, detect, respond, and recover. These controls can be classified under specific.

Nist Risk Management Framework Template Project risk management, Risk Controls vary based on the framework. No examples or combination of examples are required, and the stated examples are not the only feasible options. The nist cybersecurity framework (csf) was initially released in 2014 and last updated in 2018. Examples of controls include encrypting sensitive data, maintaining a policy to patch systems regularly, and inventorying it assets. We are excited.

The NIST Cybersecurity Framework explained inc. version 1.1 If you purchase our plain english framework, you�ll find that it�s detailed,. This article will explain what the nist framework is and how it is implemented. News and updates from nist�s computer security and applied cybersecurity divisions. For example, in 2015, the federal financial institutions. Nist manufacturing profile—nistir 8183 provides cybersecurity framework details for manufacturing including a guide for reducing.

Assessing Microsoft 365 security solutions using the NIST Cybersecurity The nist cybersecurity framework comprises five functions of cybersecurity activity, with a strong focus on incident response. As we’ve seen and discussed, the nist framework for managing cybersecurity risks through the various levels of an organization is quite complex, full of various levels and steps. “if your agency or organization hasn. Examples of outcome categories within this function include: Cybersecurity.

NIST Cybersecurity Framework is Good and Bad, Experts Say The recover function supports timely recovery to normal operations to reduce the impact from a cybersecurity event. The nist cybersecurity framework comprises five functions of cybersecurity activity, with a strong focus on incident response. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. To protect against cyberattacks, the cybersecurity team needs.

NIST 80053 rev4based Written Information Security Program (WISP) This section will cover the 6 rmf steps identified by the nist to manage cybersecurity risks effectively. Identity, protect, detect, respond, and recover. We would suggest clarifying the relationship among nist sp800 series publications in the cybersecurity framework (csf) documents. In fact, some industry regulatory bodies have published additional implementation guidance supporting the framework. The first function of the framework,.

Moving away from Tier Zero by using the NIST Cybersecurity Framework The nist cybersecurity framework is voluntary guidance, based on existing standards, guidelines, and practices to help organizations better manage and reduce cybersecurity risk. A cybersecurity framework is a list of implementable controls (both technical and process), which in totality represent a cybersecurity program. Ensuring anomalies and events are detected, and their potential impact is understood implementing security continuous monitoring capabilities.

On the Evolving Cybersecurity Landscape A Q&A with Fuze Director of This page describes reasons for using the framework, provides examples of how industry has used the framework, and highlights. Examples of outcome categories within this function include: These functions are as follows: Nist cybersecurity framework translated into plain english(title 60). Controls vary based on the framework.

NIST Cybersecurity Framework Pittsburgh Internal Audit Services What are the five elements of the nist cybersecurity framework? They support an organization in expressing its management of cybersecurity risk by addressing threats and developing by learning from past activities. News and updates from nist�s computer security and applied cybersecurity divisions. Use it to protect your organization�s critical infrastructure and to safeguard the health, safety, security, and privacy of.

NIST CSF Core Notes Info Security Memo A cybersecurity framework is a list of implementable controls (both technical and process), which in totality represent a cybersecurity program. The nist cybersecurity framework is voluntary guidance, based on existing standards, guidelines, and practices to help organizations better manage and reduce cybersecurity risk. In fact, some industry regulatory bodies have published additional implementation guidance supporting the framework. Controls vary based.

NIST Cybersecurity Framework The national institute of standards and technology, or nist, cybersecurity framework is the gold standard used by organizations to establish the fundamental controls and processes needed for optimum cybersecurity. A cybersecurity framework is a list of implementable controls (both technical and process), which in totality represent a cybersecurity program. The nist cybersecurity framework comprises five functions of cybersecurity activity, with.

5 Steps to Turn the NIST Cybersecurity Framework into Reality This section will cover the 6 rmf steps identified by the nist to manage cybersecurity risks effectively. The nist cybersecurity framework comprises five functions of cybersecurity activity, with a strong focus on incident response. Nist manufacturing profile—nistir 8183 provides cybersecurity framework details for manufacturing including a guide for reducing cybersecurity risk in accord with. A notional example of types of.

Using the NIST CSF for a Rapid Security Assessment This article will explain what the nist framework is and how it is implemented. To protect against cyberattacks, the cybersecurity team needs a thorough understanding of what. What are the five elements of the nist cybersecurity framework? Identity, protect, detect, respond, and recover. Use it to protect your organization�s critical infrastructure and to safeguard the health, safety, security, and privacy.

Three Approaches to Setting Cyber Security Budgets Examples of nist functions and categories include the following: This section will cover the 6 rmf steps identified by the nist to manage cybersecurity risks effectively. Ensuring anomalies and events are detected, and their potential impact is understood implementing security continuous monitoring capabilities to monitor cybersecurity events and verify the effectiveness of protective measures including network and physical activities The.

NIST Cyber Security Framework Stickman The nist cybersecurity framework (nist csf) consists of standards, guidelines, and best practices that help organizations improve their management of cybersecurity risk. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Nist framework is divided into 5 main functions. It fosters cybersecurity risk management and related communications among both internal and.

US government released draft for NIST cybersecurity frameworkSecurity Examples of outcome categories within this function include: The recover function supports timely recovery to normal operations to reduce the impact from a cybersecurity event. As we’ve seen and discussed, the nist framework for managing cybersecurity risks through the various levels of an organization is quite complex, full of various levels and steps. Nist manufacturing profile—nistir 8183 provides cybersecurity framework.
These functions are as follows: US government released draft for NIST cybersecurity frameworkSecurity.
If you purchase our plain english framework, you�ll find that it�s detailed,. Examples of outcome categories within this function include: For example, in 2015, the federal financial institutions. Defining the nist cybersecurity framework In fact, some industry regulatory bodies have published additional implementation guidance supporting the framework. Examples include industrial control systems, building automation systems, transportation systems, physical access control systems, physical environment monitoring systems, and physical environment measurement systems.
The elements of the framework core should be applicable to any organization that creates, processes, accesses, or stores sensitive information. For example, or retailers that carry it. For example, in 2015, the federal financial institutions. US government released draft for NIST cybersecurity frameworkSecurity, This section will cover the 6 rmf steps identified by the nist to manage cybersecurity risks effectively.







