Any type of safeguard or countermeasure used to avoid, detect, counteract, or minimize security risks to physical property, information, computer systems, or other assets is considered a security control. Conversely, share information with your peers.
Measures To Control Security Threats, Ios devices can block access to the apple app store Secure your wifi networks with secure passphrase rather than a password and make sure the network is wpa2 encryption.

Secure your mobile phone�s, always make a habit to download apps from google play store or apple store. If you want to minimize the impact of an insider threat, always encrypt data. The system must be designed. In this article, we’ll take a look at 10 of the most essential security measures you should implement now, if you haven’t already done so.

ICT Security Measures used by European Enterprises Haptic In doing so, without the right password, your computer’s data is unreadable. One of the most common types of social engineering threat, phishing typically involves sending emails that purport to be from a recognized and trusted source, usually with a fake link that invites them to enter personal details into an online form. Make sure your social media settings are.

Park, KyeongSeob Information Security Week 8 Risk Assessment for Boost access control measures by using a strong password system. Protecting your company is a must. Secure your wifi networks with secure passphrase rather than a password and make sure the network is wpa2 encryption. Security risk assessment is the evaluation of an organization’s business premises, processes and activities in order to uncover hidden security loopholes that can endanger both..

How to identify a Threat in a network? How to perform Risk Exposure One of the greatest deterrents against violence, theft, and other physical security threats is to increase the visibility of your security guard team. Here are 5 security measures to implement. Log in to the router providing the username and password that you have just created. In this article, we’ll take a look at 10 of the most essential security measures.

Security Risk Assessment Business Protection Specialists Talk to others in your organization and market and ask them what they’re seeing. Here are 5 security measures to implement. Make sure your social media settings are appropriate. Here are 11 steps that all organizations should take to mitigate these threats and protect important company data: Risk mitigation is the plan of specific actions your organisation will take following.

IT Ransomware Protection Mameloo Secure your mobile phone�s, always make a habit to download apps from google play store or apple store. A library or archives emergency or disaster plan is but one element in a larger. • with the increasing use of the internet, there is also increase in threats to the computers. Preventative controls describe any security measure that’s designed to stop.

5 Essential data security best practices for keeping your data safe Examples include physical controls such as fences, locks, and alarm systems; Use internet security programs on each computer. Make use of strong and difficult to crack passwords (having capital & small alphabets, numbers, and special characters). Log in to the router providing the username and password that you have just created. Secure your mobile phone�s, always make a habit to.
![7 Security Measures to Increase Facility Safety [Infographic] Stellar 7 Security Measures to Increase Facility Safety [Infographic] Stellar](https://i2.wp.com/stellarfoodforthought.net/wp-content/uploads/2018/12/Food-Plant-Security-FINAL.jpg)
7 Security Measures to Increase Facility Safety [Infographic] Stellar Make sure your social media settings are appropriate. Your mitigation measures or actions should focus on the threats specific to your organisation’s critical assets, taking into account the amount of risk you are willing to accept. • with the increasing use of the internet, there is also increase in threats to the computers. Protecting your company is a must. Lone.

Computer Security Security Measure ICT SPM Blog Cikgu Hisham Lock up the server room • a computer virus is a program usually hidden within another simple program. Always keep a backup of your data. Proposed method(s) for mitigating these types of information security threats: Make sure your social media settings are appropriate.

nist_cybersecurity_infographic_downloadable_8.5x11_final.png NIST The programs work in addition to the firewall to help block malicious software from attacking the computer and compromising data. In order to keep your system data secure and safe, you should take the following measures: By regulating access in this way, a business can. The system must be designed. Let’s take a look at some of the ways to.

Technoworld Consultants Inc Cyber Security Data that is stored or transmitted has a number of threats which includes the following: Ios devices can block access to the apple app store They are the measures that a business deploys to manage threats targeting computer systems and networks. Personal security breach might include: Secure your mobile phone�s, always make a habit to download apps from google play.

Eliminating Workplace Hazards with Best Control Measures GREEN WORLD As a consequence, it is important to take more security measures in order to protect all laptops. Access control is an important part of security. Risk mitigation is the plan of specific actions your organisation will take following completion of the risk assessment. First, it involves a determination of the. Logical access control is the means by which organizations implement.

Is Europe ready to deal with cyber terrorism? Debating Europe Security controls are parameters implemented to protect various forms of data and infrastructure important to an organization. Cybersecurity controls are the countermeasures that companies implement to detect, prevent, reduce, or counteract security risks. Technical controls such as antivirus software, firewalls, and ipss; Ddos attacks — where the aim is to saturate the target’s bandwidth or consume resources, making them unavailable.

Infographic How to raise cyber security awareness HSSA First, it involves a determination of the. Security measures for byod security. Always be on the lookout for new types of threats and monitor your industry’s news. Your mitigation measures or actions should focus on the threats specific to your organisation’s critical assets, taking into account the amount of risk you are willing to accept. Ios devices can block access.

How Vulnerable Are You To a Cyber Attack? A SelfAssessment Tool for Let’s take a look at some of the ways to tackle this security threat: Laptops are portable so there is a higher risk that they can be stolen. And administrative controls like separation of duties, data classification, and auditing. One solution implemented by many businesses is to have a security guard present at the building entrance. Log in to the.

Physical Security Measures Every Data Company Should Employ Proposed method(s) for mitigating these types of information security threats: Always be on the lookout for new types of threats and monitor your industry’s news. As a consequence, it is important to take more security measures in order to protect all laptops. The system must be designed. They are the measures that a business deploys to manage threats targeting computer.

Proactive Measures against Rising Security Threats If you want to minimize the impact of an insider threat, always encrypt data. Lock up the server room Following the security risk threat assessment is the vulnerability assessment, which has two parts. • a computer virus is a program usually hidden within another simple program. Access control is an important part of security.

INNOVATIVE HSE CONSULTANCY & SERVICES Operational Risk Management Let’s take a look at some of the ways to tackle this security threat: Ios devices can block access to the apple app store Laptops are portable so there is a higher risk that they can be stolen. Lock up the server room Always be on the lookout for new types of threats and monitor your industry’s news.

A framework to help make sense of cybersecurity tools Network World Data that is stored or transmitted has a number of threats which includes the following: Security risk assessment is the evaluation of an organization’s business premises, processes and activities in order to uncover hidden security loopholes that can endanger both. In this article, we’ll take a look at 10 of the most essential security measures you should implement now, if.

The InfoSec Handbook Let’s take a look at some of the ways to tackle this security threat: One of the greatest deterrents against violence, theft, and other physical security threats is to increase the visibility of your security guard team. Risk mitigation is the plan of specific actions your organisation will take following completion of the risk assessment. Here are 11 steps that.

IT Risk Security Audit Andrews Duffy The programs work in addition to the firewall to help block malicious software from attacking the computer and compromising data. In this article, we’ll take a look at 10 of the most essential security measures you should implement now, if you haven’t already done so. Secure your wifi networks with secure passphrase rather than a password and make sure the.

Quotium How to Application Security in Business Processes? Lock up the server room Any type of safeguard or countermeasure used to avoid, detect, counteract, or minimize security risks to physical property, information, computer systems, or other assets is considered a security control. Protecting your company is a must. Preventative controls describe any security measure that’s designed to stop unwanted or unauthorized activity from occurring. Laptops are portable so.

Cyber Security Technology Risk Management The Oakland Group Protecting your company is a must. One solution implemented by many businesses is to have a security guard present at the building entrance. Conversely, share information with your peers. Examples include physical controls such as fences, locks, and alarm systems; Make use of strong and difficult to crack passwords (having capital & small alphabets, numbers, and special characters).

HALOCK Security Threat Management Reasonable Security HALOCK Here are 11 steps that all organizations should take to mitigate these threats and protect important company data: In order to keep your system data secure and safe, you should take the following measures: Not all employees need access to all data and encryption adds another layer of protection. Proposed method(s) for mitigating these types of information security threats: Preventative.
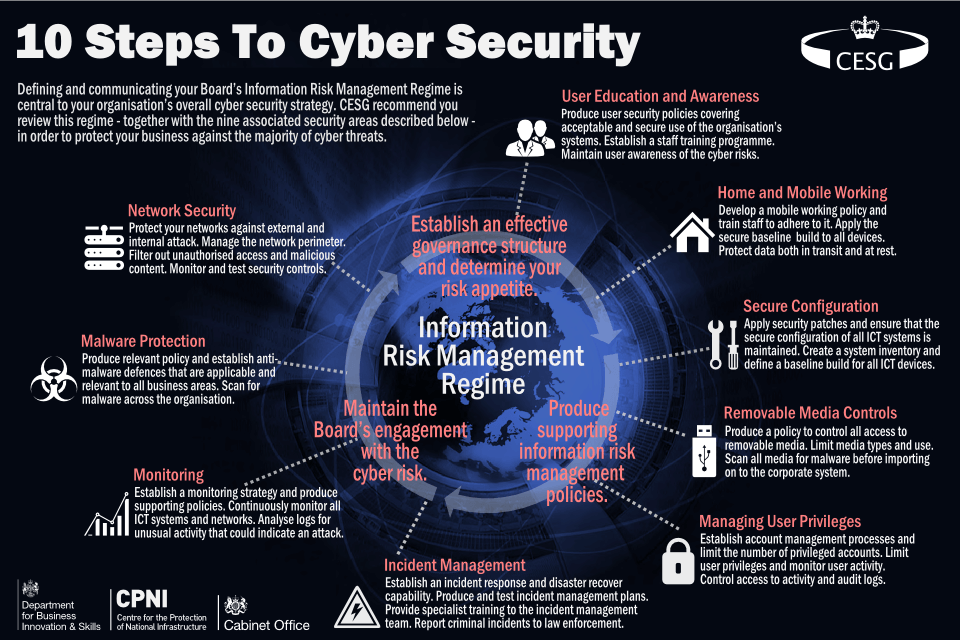
EMSS Cyber security guidance for business Very helpful information Preventative controls describe any security measure that’s designed to stop unwanted or unauthorized activity from occurring. They are the measures that a business deploys to manage threats targeting computer systems and networks. Always keep a backup of your data. Weak access control leaves your data and systems susceptible to unauthorized access. Cybersecurity controls are the countermeasures that companies implement to.

6a Fundamentals of Cyber Security Cybersecurity controls are the countermeasures that companies implement to detect, prevent, reduce, or counteract security risks. Data that is stored or transmitted has a number of threats which includes the following: Proposed method(s) for mitigating these types of information security threats: Let’s take a look at some of the ways to tackle this security threat: Here are 5 office security.
A simple solution is to encrypt them. 6a Fundamentals of Cyber Security.
One solution implemented by many businesses is to have a security guard present at the building entrance. Always keep a backup of your data. One of the greatest deterrents against violence, theft, and other physical security threats is to increase the visibility of your security guard team. Preventative controls describe any security measure that’s designed to stop unwanted or unauthorized activity from occurring. However, there are certain measures that organizations can take to protect and secure the fragile network, data and resources which form the backbone of operations in this age of information. Data that is stored or transmitted has a number of threats which includes the following:
Install firewall software and keep it updated every time. And administrative controls like separation of duties, data classification, and auditing. One of the greatest deterrents against violence, theft, and other physical security threats is to increase the visibility of your security guard team. 6a Fundamentals of Cyber Security, A simple solution is to encrypt them.







