Mirai botnet the 2016 mirai botnet is one of the more infamous iot security breaches, in part because it was the largest attack we’ve seen so far, but also because the code is still out there. They also notified their findings to amazon before the presentation, and amazon pushed a security patch to fix the issues.
Iot Attacks Examples, Verizon’s data breach digest 2017 report details the example of an unnamed university where the network was flooded with domain name service (dns) requests for seafood restaurants. Android devices are more vulnerable and account for 26.64% of infections, according to nokia.

Use a compromised iot device to attack other devices, systems, and applications. Need to brush up on the fundamentals of iot security? The attack that targeted a dns service provider dyn, using a botnet of iot devices. 10 types of iot cyber security attacks.

What is IOT ? How Does it Work ? Advantages and Future of IOT TECH POINT 10 types of iot cyber security attacks. Whilst it sounds like a student prank, it was actually an outside attack by hackers which used 5,000 iot. If the network is insecure authentication. Iot connects a variety of sensors, alarms, cameras, lights, and microphones to provide 24/7/365 security—all of which can be controlled from a smart phone. Verizon’s data breach digest.
![]()
IoT Devices Under Constant Attack Silicon UK Tech News For example, in its 2017 data breach digest report, verizon provided the example of a major university that suffered a botnet attack that was the result of more than 5,000 connected devices, nearly all of which were on the university’s network. Overall, the number of compromised iot devices increased by 100% in 2020. That’s a very nice way of saying.

Figure 1 from Securing Heterogeneous IoT with Intelligent DDoS Attack Iot connects a variety of sensors, alarms, cameras, lights, and microphones to provide 24/7/365 security—all of which can be controlled from a smart phone. Iot attacks can be termed as an attempt to expose, alter, disable or gain unauthorized access or steal information from the connected devices or thing. They test the most generic and used passwords and thus be.
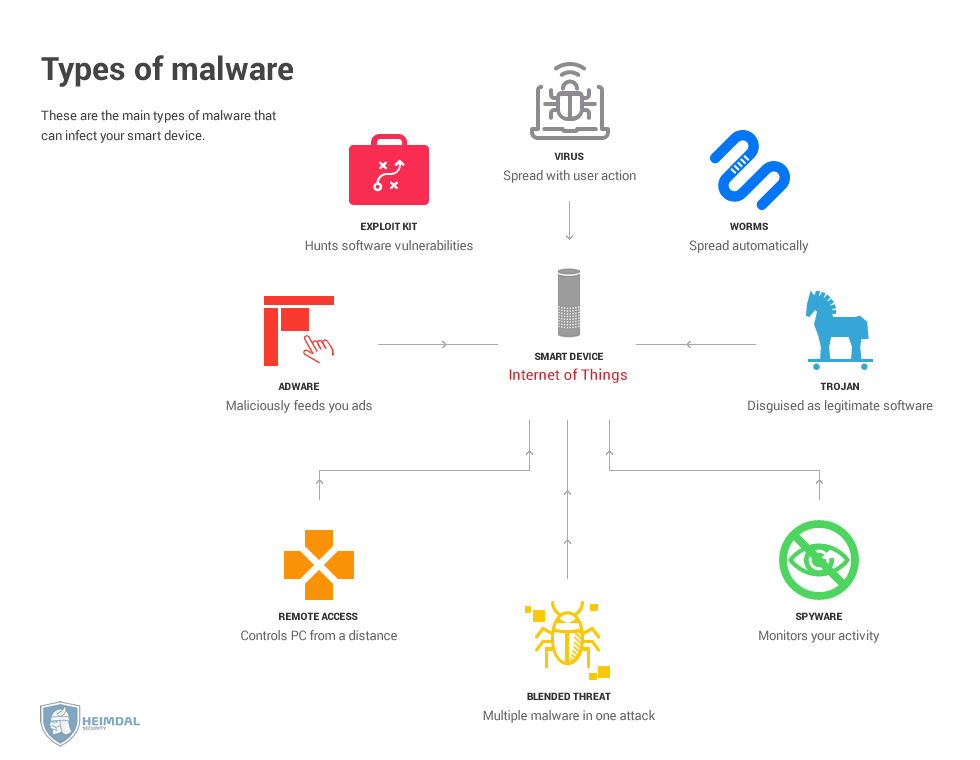
IoT Security All You Need to Know and Apply If the network is insecure authentication. 10 types of iot cyber security attacks. Examples of passive attacks include traffic analysis, monitoring, node destruction and malfunction; In this case, they could obtain data. For example, one vulnerable iot device is enough to cripple an entire network and gain access to sensitive information.

Arm launches first set of threat models for PSA IoT blog How do iot attacks work? They also notified their findings to amazon before the presentation, and amazon pushed a security patch to fix the issues. Use a compromised iot device to attack other devices, systems, and applications. This attack is just an example of what can happen to iot devices with poor security. The team used amazon echo smart speakers.

Security in IoT devices MIPS A thermometer in a lobby aquarium. In 2021 the iot threat landscape continued to evolve. Examples of physical layer attacks include node tampering, jamming and replication. Mirai botnet attack on iot devices. Example such devices could be thermostats, medical devices, wearables, smart appliances, office equipments, etc.,

When the IoT Attacks Four Examples of the Highest Security Stakes We It always seems that casinos are some of the most secure organizations in the world, but they can be hacked as well These attacks interfere with the device making them the vulnerable terminal in iot. If such a device is connected to a corporate network, hackers can gain access to the network and extract all the valuable data. In october.

How Cybercriminals Are IoT Attack Tools Now If the network is insecure authentication. Hackers pushed the boundaries in terms of what was thought technological possible, while corporate device manufacturers had their brand dragged through the mud, as their legacy security mechanisms didn’t stand a chance. For example, in its 2017 data breach digest report, verizon provided the example of a major university that suffered a botnet attack.

The IoT Attack Surface Threats and Security Solutions Security News Examples of physical layer attacks include node tampering, jamming and replication. Need to brush up on the fundamentals of iot security? Example such devices could be thermostats, medical devices, wearables, smart appliances, office equipments, etc., The attack that targeted a dns service provider dyn, using a botnet of iot devices. How do iot attacks work?

IoT Security IoT Traffic Analysis Iot devices located at inaccessible locations without the feature to be. These attacks interfere with the device making them the vulnerable terminal in iot. Verizon’s data breach digest 2017 report details the example of an unnamed university where the network was flooded with domain name service (dns) requests for seafood restaurants. Below are 10 of the best examples of how.

DDoS (Distributed Denial Of Service) Attack And Prevention ShecLabs If the network is insecure authentication. 10 types of iot cyber security attacks. Use a compromised iot device to attack other devices, systems, and applications. For example, these devices can be anything from industrial tools, machinery, or vehicles to innocuous connected things such as smart tv�s or garage door openers. These attacks interfere with the device making them the vulnerable.

Example of a smart meter phishing attack via compromised update and Home security the internet of things is the key driver behind a completely smart and secure home. Iot devices located at inaccessible locations without the feature to be. In this case, cybercriminals use brute force to try to access them. Verizon’s data breach digest 2017 report details the example of an unnamed university where the network was flooded with domain.

IoT Security 10 Challenges of Securing IoT Communications PubNub Overall, the number of compromised iot devices increased by 100% in 2020. The most common iot attack today is the mirai malware, which originated in 2016. How do iot attacks work? Whilst it sounds like a student prank, it was actually an outside attack by hackers which used 5,000 iot. For example, one vulnerable iot device is enough to cripple.
![[Infographic] 10 MustKnow IoT Cybersecurity Stats BehrTech Blog [Infographic] 10 MustKnow IoT Cybersecurity Stats BehrTech Blog](https://i2.wp.com/behrtech.com/wp-content/uploads/2019/04/IoT-cybersecurity-1.png)
[Infographic] 10 MustKnow IoT Cybersecurity Stats BehrTech Blog Verizon’s data breach digest 2017 report details the example of an unnamed university where the network was flooded with domain name service (dns) requests for seafood restaurants. Physical attacks occur when iot devices can be physically accessed by anyone. They test the most generic and used passwords and thus be able to compromise the teams of the victims. If the.
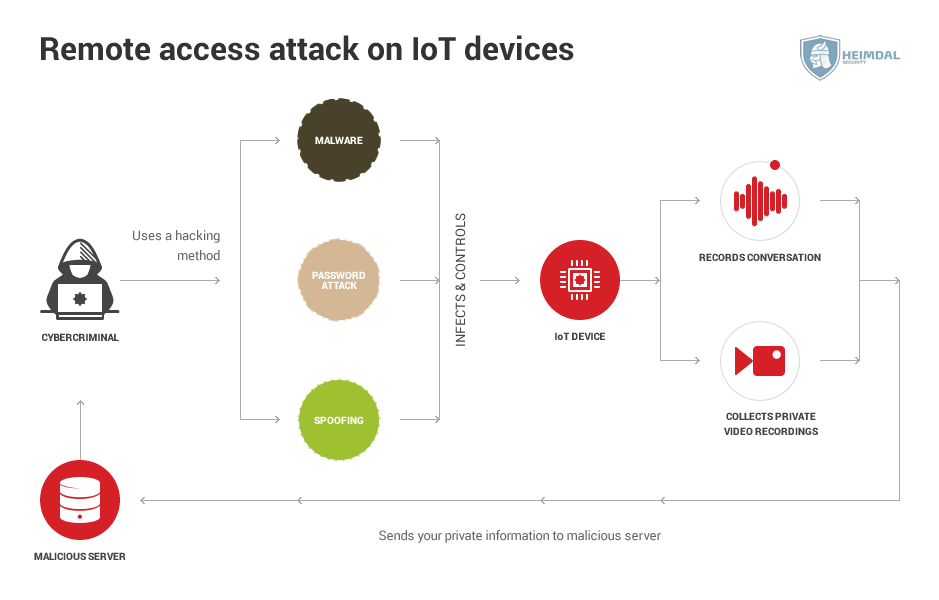
IoT Security All You Need to Know and Apply The team used amazon echo smart speakers to present their attack program. This attack is just an example of what can happen to iot devices with poor security. Mirai botnet attack on iot devices. Hackers pushed the boundaries in terms of what was thought technological possible, while corporate device manufacturers had their brand dragged through the mud, as their legacy.

How IoT works? For example, in its 2017 data breach digest report, verizon provided the example of a major university that suffered a botnet attack that was the result of more than 5,000 connected devices, nearly all of which were on the university’s network. A thermometer in a lobby aquarium. It always seems that casinos are some of the most secure organizations in.

of IoT attacks increasing Study itnext.in Examples of physical layer attacks include node tampering, jamming and replication. We heard about the mirai. For example, these devices can be anything from industrial tools, machinery, or vehicles to innocuous connected things such as smart tv�s or garage door openers. Need to brush up on the fundamentals of iot security? Let�s move to the privacy challenge.

(PDF) Toward a Lightweight Intrusion Detection System for the This attack is just an example of what can happen to iot devices with poor security. Hackers pushed the boundaries in terms of what was thought technological possible, while corporate device manufacturers had their brand dragged through the mud, as their legacy security mechanisms didn’t stand a chance. Take a look at these crazy examples of iot hacking and vulnerabilities.

A Vision for Secure IoT CableLabs The botnet is named after the mirai malware that it used to infect connected devices. Insufficient data protection (communication and storage) the most frequent concerns in the data security of iot applications are due to insecure communications and data storage. The most common security risks Verizon’s data breach digest 2017 report details the example of an unnamed university where the.

IoT environment threat dimensions. Download Scientific Diagram Here are just a few examples of iot security breaches. These attacks interfere with the device making them the vulnerable terminal in iot. Verizon’s data breach digest 2017 report details the example of an unnamed university where the network was flooded with domain name service (dns) requests for seafood restaurants. The botnet is named after the mirai malware that it.

Different types of malware attacks in IoT/IoMT environment Download Let’s take a look at four real life examples of the iot being hacked. In addition, windows computers are responsible for 38.92% of all infections. The researchers hacked the speaker by adding a malicious device embedded with an attack program. In october 2016, a hacker found a vulnerability in a specific model of security cameras. Iot hacking can be extremely.

Largest DDoS Attack Ever Delivered by of Hijacked IoT Devices In october 2016, a hacker found a vulnerability in a specific model of security cameras. Example such devices could be thermostats, medical devices, wearables, smart appliances, office equipments, etc., The team used amazon echo smart speakers to present their attack program. This attack is just an example of what can happen to iot devices with poor security. Iot attacks can.

5 examples why IoT devices need a voice Thales blog As we’ve seen from the four examples in this blog some of the top reasons for iot security breaches include: How do iot attacks work? The researchers hacked the speaker by adding a malicious device embedded with an attack program. Overall, the number of compromised iot devices increased by 100% in 2020. Here are just a few examples of iot.

Does Japan Get Industrial IoT? EE Times Asia Check out our complete guide to iot security, or visit our solutions page to l earn how byos can help. In addition, windows computers are responsible for 38.92% of all infections. We heard about the mirai. Of course , information theft is another threat present on iot devices. Overall, the number of compromised iot devices increased by 100% in 2020.

Five Steps to Successful Threat Modelling of Things Iot connects a variety of sensors, alarms, cameras, lights, and microphones to provide 24/7/365 security—all of which can be controlled from a smart phone. 10 types of iot cyber security attacks. Examples of physical layer attacks include node tampering, jamming and replication. Android devices are more vulnerable and account for 26.64% of infections, according to nokia. Media titans like twitter,.
In addition, windows computers are responsible for 38.92% of all infections. Five Steps to Successful Threat Modelling of Things.
Example such devices could be thermostats, medical devices, wearables, smart appliances, office equipments, etc., The attack that targeted a dns service provider dyn, using a botnet of iot devices. In 2021 the iot threat landscape continued to evolve. Media titans like twitter, reddit, cnn, and netflix were affected. The most common security risks #1: Hackers pushed the boundaries in terms of what was thought technological possible, while corporate device manufacturers had their brand dragged through the mud, as their legacy security mechanisms didn’t stand a chance.
Iot attacks can be termed as an attempt to expose, alter, disable or gain unauthorized access or steal information from the connected devices or thing. If the network is insecure authentication. Overall, the number of compromised iot devices increased by 100% in 2020. Five Steps to Successful Threat Modelling of Things, The iot botnet attack exploits the insecure iot devices with open telnet ports and weak/default credentials to build a botnet.







