Considering the above challenges, the scope of this special issue of cryptography: Several iot security attacks are analyzed, and a taxonomy of the security requirements based on the attacks’ purposes is proposed.
Internet Of Things (Iot) Taxonomy Of Security Attacks, The taxonomy of the most relevant and current iot security attacks is presented for application, network, and physical layers. Taxonomy of security attacks within iot networks is constructed to assist iot developers for better awareness of the risk of security flaws so that better protections shall be incorporated.

A survey and taxonomy abstract: Internet of things (iot) technology is prospering and entering every part of our lives, be it education, home, vehicles, or healthcare. Resilience against sensing node capture attack; Data storage and processing are essential components of the iot ecosystem.

Security in IoT devices MIPS The internet of things (iot) regulates millions of terabytes of data for everyday commercial, industrial, technical and personal usage. Introduction internet of things (iots) is an application development domain that incorporates a range of technologies. Data storage and processing are essential components of the iot ecosystem. The internet of things (iot) comprises a complex network of smart devices, which frequently.

What is IoT Security? Adapt IT A survey and taxonomy abstract: The rest of the paper is organized as follows. This section focuses on the taxonomy of various possible security threats and their countermeasures at different layers of iot security. “passive attacks” and “active attacks”. With the developments in the technology, internet of things (iot) become important part of human life.

96 Percent of IT Security Professionals Expect an Increase in The number of devices connected to the internet, those with a digital identity, is increasing day by day. Keeping up with the burgeoning internet of things (iot) requires staying up to date on the latest network attack trends in dynamic and complicated cyberspace, and take them into account while developing holistic information security (is) approaches for the iot. The deployment.

(PDF) A Survey of Security Challenges, Attacks Taxonomy and Advanced Internet of things (iot) technology is prospering and entering every part of our lives, be it education, home, vehicles, or healthcare. Figure 2 and table 1 highlight the comparative analysis of various security threats, their implications, level of attack, occurrence in architecture model, security principles compromised and their countermeasures. “passive attacks” and “active attacks”. A survey and taxonomy abstract: Taxonomy.
![An overview of IoMT [60] 3. SECURITY AND PRIVACY THREATS IN IOT An overview of IoMT [60] 3. SECURITY AND PRIVACY THREATS IN IOT](https://i2.wp.com/www.researchgate.net/profile/Prajoy_Podder/publication/343010716/figure/download/fig2/AS:914275224801280@1594991608800/An-overview-of-IoMT-60-3-SECURITY-AND-PRIVACY-THREATS-IN-IOT-Security-and-privacy.jpg)
An overview of IoMT [60] 3. SECURITY AND PRIVACY THREATS IN IOT Internet of things (iot) technology is prospering and entering every part of our lives, be it education, home, vehicles, or healthcare. Therefore, a detailed review of security attacks towards wsns and iot, along with the techniques for prevention, detection, and mitigation of those attacks are provided in this paper. The first remarkable aspect of iots came from the term that.

Pin on Cyber Attack, Cyber Crime, Cyber Security, News, Blogs The internet of things (iot) comprises a complex network of smart devices, which frequently exchange data through. Raw data about iot apps and devices is collected using network host scanning and vulnerability scanning technologies. Resilience against sensing node capture attack; This provides an analytical basis for the protection of different iot applications. Request pdf | internet of things:
![Classification of the IoT Attacks [70], [71]. Download Scientific Diagram Classification of the IoT Attacks [70], [71]. Download Scientific Diagram](https://barokoks.github.io/img/placeholder.svg)
Classification of the IoT Attacks [70], [71]. Download Scientific Diagram Hence, strengthening iot’s security and preserving users’ privacy is a major challenge. This provides an analytical basis for the protection of different iot applications. Taxonomy of security attacks within iot networks is constructed to assist iot developers for better awareness of the risk of security flaws so that better protections shall be incorporated. The internet of things (iot) has disrupted.

Taxonomy of CyberPhysical Attacks on Manufacturing Systems. Download Taxonomy of security attacks in internet of things iot development boards and sensors as well as cloud subscriptions are used in this study to build up an experimental setup. Taxonomy of various security attacks in iot based on architecture layers 3.1 perception layer attacks rfid systems do not have reliable authentication technologies, which allow unauthorized attackers to easily access tags.

of Things (IoT) Whitepaper définition IoT Since the communication often takes place over the internet, it is vulnerable to various security threats in an iot. Heterogeneity, scalability, quality of service, security requirements, and many more. A survey and taxonomy abstract: The deployment of a large number of objects adhered to the internet has unlocked the vision of the smart world around us, thereby paving a road.

(PDF) Anatomy of Threats to The of Things The internet of things (iot) is a system of physical as well as virtual objects (each with networking capabilities incorporated) that are interconnected to exchange and collect information locally or remotely over the internet. Internet of things (iot) is a paradigm that has the capability to revolutionize on everyday life, in sectors of ranging from our homes, health, transport, industry,.
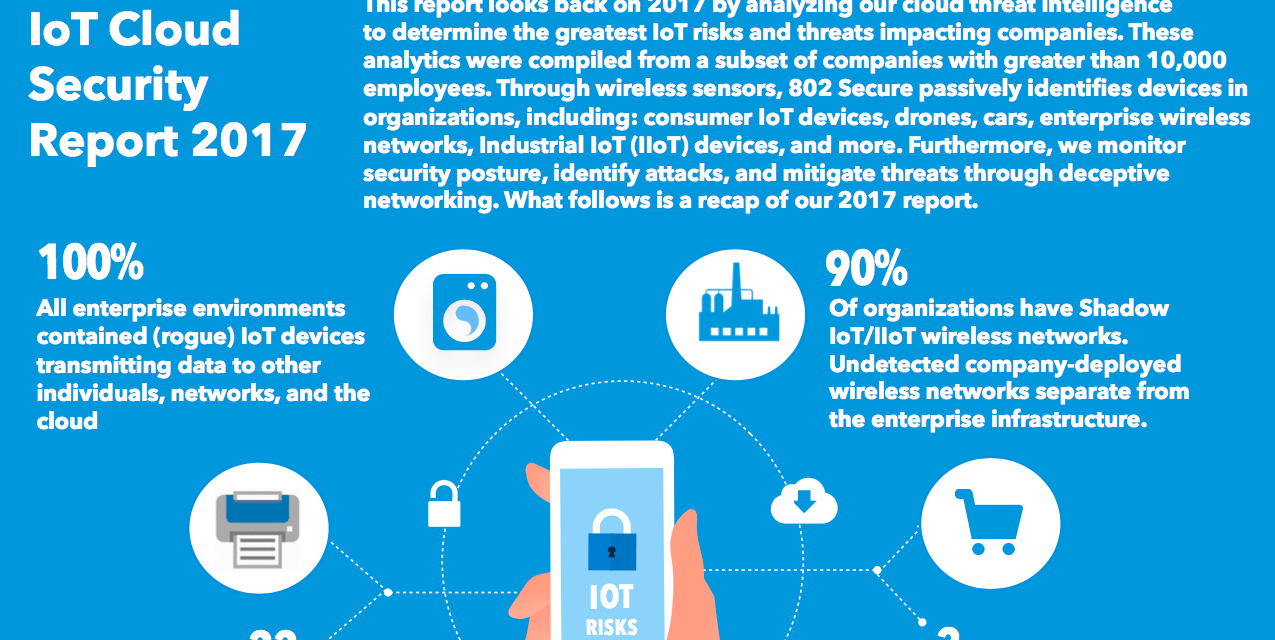
Beware the Shadow IoT Security threats through of Things The taxonomy of the most relevant and current iot security attacks is presented for application, network, and physical layers. Figure 2 and table 1 highlight the comparative analysis of various security threats, their implications, level of attack, occurrence in architecture model, security principles compromised and their countermeasures. Keeping up with the burgeoning internet of things (iot) requires staying up to.

Typical IoT Attacks and Effects. Download Scientific Diagram “passive attacks” and “active attacks”. The internet of things (iot) is a system of physical as well as virtual objects (each with networking capabilities incorporated) that are interconnected to exchange and collect information locally or remotely over the internet. Now, various security issues are considered as major problem for a full. Unfortunately, this has attracted the attention of cybercriminals who.

ioT attacks 10 things you need to know Cybersecurity Observatory Request pdf | internet of things: Taxonomy of security attacks in internet of things iot development boards and sensors as well as cloud subscriptions are used in this study to build up an experimental setup. Internet of things (iot) is a paradigm that has the capability to revolutionize on everyday life, in sectors of ranging from our homes, health, transport,.

The IoT Attack Surface Threats and Security Solutions Security News Keeping up with the burgeoning internet of things (iot) requires staying up to date on the latest network attack trends in dynamic and complicated cyberspace, and take them into account while developing holistic information security (is) approaches for the iot. Taxonomy of various security attacks in iot based on architecture layers 3.1 perception layer attacks rfid systems do not have.

IoT Security 10 Challenges of Securing IoT Communications PubNub Hence, strengthening iot’s security and preserving users’ privacy is a major challenge. Therefore, a detailed review of security attacks towards wsns and iot, along with the techniques for prevention, detection, and mitigation of those attacks are provided in this paper. The zois security taxonomy for iot may also be usable for operational technology (ot). Former security analyses have suggested that.

(PDF) A Survey of Security Challenges, Attacks Taxonomy and Advanced Hence, strengthening iot’s security and preserving users’ privacy is a major challenge. Taxonomy of various security attacks in iot based on architecture layers 3.1 perception layer attacks rfid systems do not have reliable authentication technologies, which allow unauthorized attackers to easily access tags [8, 9, 10]. Due to multiple vulnerabilities in the iot foundations, many targeted attacks are. The internet.

This Isn’t a Tech Thriller IoT Attacks Are Real The rest of the paper is organized as follows. Request pdf | internet of things: Former security analyses have suggested that the gateways in lorawan in their current state are susceptible to a wide variety of malicious attacks, which can be notoriously. Since the communication often takes place over the internet, it is vulnerable to various security threats in an.

Is The IoT Making Us Vulnerable? Techno FAQ Therefore, a detailed review of security attacks towards wsns and iot, along with the techniques for prevention, detection, and mitigation of those attacks are provided in this paper. The deployment of a large number of objects adhered to the internet has unlocked the vision of the smart world around us, thereby paving a road towards automation and humongous data generation.

The Four Types of IoT Attacks. A Taxonomy of IoT Attacks by Bob Young Internet of things (iot) is a paradigm that has the capability to revolutionize on everyday life, in sectors of ranging from our homes, health, transport, industry, entertainment to interaction. This provides an analytical basis for the protection of different iot applications. The internet of things (iot) apps accumulate a large amount of data. In this text, attacks are categorized and.

Taxonomy for the of Things (IoT) Zero Outage Security management takes a back. Since the communication often takes place over the internet, it is vulnerable to various security threats in an iot. Taxonomy of security attacks within iot networks is constructed to assist iot developers for better awareness of the risk of security flaws so that better protections shall be incorporated. Due to multiple vulnerabilities in the iot.

(PDF) of Things Security Layered classification of attacks Data storage and processing are essential components of the iot ecosystem. Therefore, a detailed review of security attacks towards wsns and iot, along with the techniques for prevention, detection, and mitigation of those attacks are provided in this paper. The zois security taxonomy for iot may also be usable for operational technology (ot). Taxonomy of security attacks in internet of.

Security Taxonomy in IoT Device lifecycle Download Scientific Diagram Introduction internet of things (iots) is an application development domain that incorporates a range of technologies. The taxonomy of the most relevant and current iot security attacks is presented for application, network, and physical layers. Internet of things (iot) technology is prospering and entering every part of our lives, be it education, home, vehicles, or healthcare. The internet of things.

A Classification of Security Threats and Controls in IoT Download Wherever the data is present online, one can use secure sockets layer protocol, or ssl, to fix this iot security The internet of things (iot) has disrupted the it landscape drastically, and long range wide area network (lorawan) is one specification that enables these iot devices to have access to the internet. Data storage and processing are essential components of.

New IoT Threat Map Will Haunt Your Dreams However, it is not well defined and secure. This provides an analytical basis for the protection of different iot applications. Taxonomy of various security attacks in iot based on architecture layers 3.1 perception layer attacks rfid systems do not have reliable authentication technologies, which allow unauthorized attackers to easily access tags [8, 9, 10]. Due to multiple vulnerabilities in the.

(PDF) of Things Security Layered classification of attacks Heterogeneity, scalability, quality of service, security requirements, and many more. The internet of things (iot) apps accumulate a large amount of data. Former security analyses have suggested that the gateways in lorawan in their current state are susceptible to a wide variety of malicious attacks, which can be notoriously. “passive attacks” and “active attacks”. Taxonomy of iot security and vulnerabilities.
Introduction internet of things (iots) is an application development domain that incorporates a range of technologies. (PDF) of Things Security Layered classification of attacks.
Keeping up with the burgeoning internet of things (iot) requires staying up to date on the latest network attack trends in dynamic and complicated cyberspace, and take them into account while developing holistic information security (is) approaches for the iot. The most of this information is personal and must be encrypted. Several iot security attacks are analyzed, and a taxonomy of the security requirements based on the attacks’ purposes is proposed. Resilience against sensing node capture attack; The survey discusses a systematic summary of the iot security challenges and goals. Taxonomy of security attacks within iot networks is constructed to assist iot developers for better awareness of the risk of security flaws so that better protections shall be incorporated.
Due to multiple vulnerabilities in the iot foundations, many targeted attacks are. The internet of things (iot) has been rapidly evolving towards making a greater impact on everyday life to large industrial systems. Security management takes a back. (PDF) of Things Security Layered classification of attacks, The internet of things (iot) has disrupted the it landscape drastically, and long range wide area network (lorawan) is one specification that enables these iot devices to have access to the internet.







