Ad a fully iso 27001 certified process to help you mitigate threats. In addition, patch management helps identify areas within your organization’s critical assets requiring security patches.
Cybersecurity Examples, Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption. Data is most vulnerable during process or transport, which offers a prime opportunity for attack.

There are other examples of microsoft�s software catching these attacks early. This type of attack is often seen in office buildings, where an attacker will follow someone with an access. A cyber security engineer performs many of the same tasks but is working at a higher level. To quote a definition from pwc:

Multimedia Gallery Infographic showing how NSFsupported Cyber security may also be referred to as information technology security. Also, to make their computer systems safe from cyber threats. Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption. The technology you’ll use to prevent and combat cybersecurity attacks, like dns filtering, malware protection, antivirus software, firewalls and email security solutions. These standard.

A framework to help make sense of cybersecurity tools Network World 6 examples of security policies. An effective cyber security executive summary includes several essential sections. Tutorials, references, and examples are constantly reviewed to avoid errors, but we cannot warrant full correctness of all content. “cyber risk is any risk associated with financial loss, disruption or damage to the reputation of an organization from failure, unauthorized or erroneous use of its.

Cyber Security Degrees These standard examples are used by device manufacturers. Welcome to this introductory course in cyber security. 6 examples of security policies. Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. Tutorials, references, and examples are constantly reviewed to avoid errors, but we cannot warrant.

Are You Cyber Secured? Be Aware of Potential Cyber Attacks ECS Here are a few recent examples of cyber attacks that had a global impact. This type of attack is often seen in office buildings, where an attacker will follow someone with an access. This course serves as an excellent primer to the many different domains of cyber security. The famous capital one breach provides an example, as it resulted from.

Cybersecurity example 2 Drupal But nowadays big companies, governments also use cybersecurity frameworks. The cybersecurity threats landscape is growing and increasing its negative impacts on companies, with cybercrime causing nearly $1 trillion in damage in 2020, according to “the hidden costs of cybercrime” report by mcafee. This course serves as an excellent primer to the many different domains of cyber security. Posted at 00:16h.

Cybersecurity example 3 Drupal Ad a fully iso 27001 certified process to help you mitigate threats. Eavesdropping attack begins with the interception of network traffic. The famous capital one breach provides an example, as it resulted from problems with capital one’s cloud migration plan. The massive french insurance and financial services company axa it relies on the cybersecurity firm darktrace to deal with online.

Sample Cyber Security Business Plan Google Slides & Ppt Template Cyber Eavesdropping attack begins with the interception of network traffic. 6 cybersecurity kpi examples for your next report: Welcome to this introductory course in cyber security. There are other examples of microsoft�s software catching these attacks early. The famous capital one breach provides an example, as it resulted from problems with capital one’s cloud migration plan.

Cybersecurity Threats Posted at 00:16h in cyber security by stefan schulz. The cybersecurity threats landscape is growing and increasing its negative impacts on companies, with cybercrime causing nearly $1 trillion in damage in 2020, according to “the hidden costs of cybercrime” report by mcafee. The massive french insurance and financial services company axa it relies on the cybersecurity firm darktrace to deal.

Cyber Security Definition Examples and Forms The cybersecurity threats landscape is growing and increasing its negative impacts on companies, with cybercrime causing nearly $1 trillion in damage in 2020, according to “the hidden costs of cybercrime” report by mcafee. Eavesdropping attack begins with the interception of network traffic. These cybersecurity examples are just a sampling of the threats and defense steps out there today. To quote.

What is a cyber attack? Recent examples show disturbing trends CSO Online Ad a fully iso 27001 certified process to help you mitigate threats. Ad a fully iso 27001 certified process to help you mitigate threats. While using w3schools, you agree to have read and accepted our. In this type of cyber crime, individuals attempt to steal information that computers, smartphones, or other devices receive or send. Security patches help prevent threat.

Cyber Security Awareness Training the new norm? DC Security patches help prevent threat actor exploitation of security gaps and vulnerabilities, mitigating occurrences of threat attacks. Understanding these basics is the first step to. A cyber security engineer performs many of the same tasks but is working at a higher level. Data is most vulnerable during process or transport, which offers a prime opportunity for attack. Welcome to this.

Cybersecurity Creating the Plan TechNation Common examples of network security implementation: Ad a fully iso 27001 certified process to help you mitigate threats. But nowadays big companies, governments also use cybersecurity frameworks. Cyberterrorism is intended to undermine electronic systems to cause panic or fear. The massive french insurance and financial services company axa it relies on the cybersecurity firm darktrace to deal with online threats.

A Beginner�s Guide To Cybersecurity Framework Edureka While using w3schools, you agree to have read and accepted our. An effective cyber security executive summary includes several essential sections. It is to make the computer system safe from online threats. Understanding these basics is the first step to. At its most basic level, however, cyber risk is the risk of damage to an organization through its information systems.

Three Approaches to Setting Cyber Security Budgets Understanding these basics is the first step to. 6 cybersecurity kpi examples for your next report: Piggybacking is a social engineering attack in which an attacker uses another person’s legitimate access to a physical or electronic location to gain unauthorized access themselves. The famous capital one breach provides an example, as it resulted from problems with capital one’s cloud migration.

Cyber Security Is It Identity Theft or Identity Gift? Part 1 The technology you’ll use to prevent and combat cybersecurity attacks, like dns filtering, malware protection, antivirus software, firewalls and email security solutions. The technology your data lives on that needs your protection, like computers,. These cybersecurity examples are just a sampling of the threats and defense steps out there today. A cyber security engineer performs many of the same tasks.

Cybersecurity Introduction Global ZData Features These standard examples are used by device manufacturers. This type of attack is often seen in office buildings, where an attacker will follow someone with an access. At its most basic level, however, cyber risk is the risk of damage to an organization through its information systems. Understanding these basics is the first step to. Security patches help prevent threat.

Cybersecurity example 1 Drupal At its most basic level, however, cyber risk is the risk of damage to an organization through its information systems. A cyber security engineer performs many of the same tasks but is working at a higher level. “cyber risk is any risk associated with financial loss, disruption or damage to the reputation of an organization from failure, unauthorized or erroneous.

Cyber Security and Information Security KPI Examples Ad a fully iso 27001 certified process to help you mitigate threats. A cyber security engineer performs many of the same tasks but is working at a higher level. Also, to make their computer systems safe from cyber threats. Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption. This course serves as an excellent.

Cyber Security Strategy Template Ad a fully iso 27001 certified process to help you mitigate threats. Understanding these basics is the first step to. The technology you’ll use to prevent and combat cybersecurity attacks, like dns filtering, malware protection, antivirus software, firewalls and email security solutions. Improved cybersecurity policies (and the distribution of said policies) can help employees better understand how to maintain the.

Risk Register Examples for Cybersecurity Leaders Security Boulevard Tutorials, references, and examples are constantly reviewed to avoid errors, but we cannot warrant full correctness of all content. The cybersecurity threats landscape is growing and increasing its negative impacts on companies, with cybercrime causing nearly $1 trillion in damage in 2020, according to “the hidden costs of cybercrime” report by mcafee. In addition, patch management helps identify areas within.

10 best cybersecurity poster examples images on Pinterest Computer 6 examples of security policies. Here are a few recent examples of cyber attacks that had a global impact. This type of cyber crime is also known as sniffing or snooping. In a security context, mean time to detect (mttd) is a measurement of how long it takes the cybersecurity team or security operations center to become aware of a..
![[Withdrawn] Common Cyber Attacks Summary GOV.UK [Withdrawn] Common Cyber Attacks Summary GOV.UK](https://i2.wp.com/assets.publishing.service.gov.uk/government/uploads/system/uploads/image_data/file/35290/common_cyber_attacks.png)
[Withdrawn] Common Cyber Attacks Summary GOV.UK “cyber risk is any risk associated with financial loss, disruption or damage to the reputation of an organization from failure, unauthorized or erroneous use of its information systems.”. The famous capital one breach provides an example, as it resulted from problems with capital one’s cloud migration plan. Cyber security refers to the body of technologies, processes, and practices designed to.

Examples of National Cyber Security Strategies Download Table Eavesdropping attack begins with the interception of network traffic. Common examples of network security implementation: Ad a fully iso 27001 certified process to help you mitigate threats. Deep learning methods such as lstm have been successfully applied to cyber security issues. The massive french insurance and financial services company axa it relies on the cybersecurity firm darktrace to deal with.
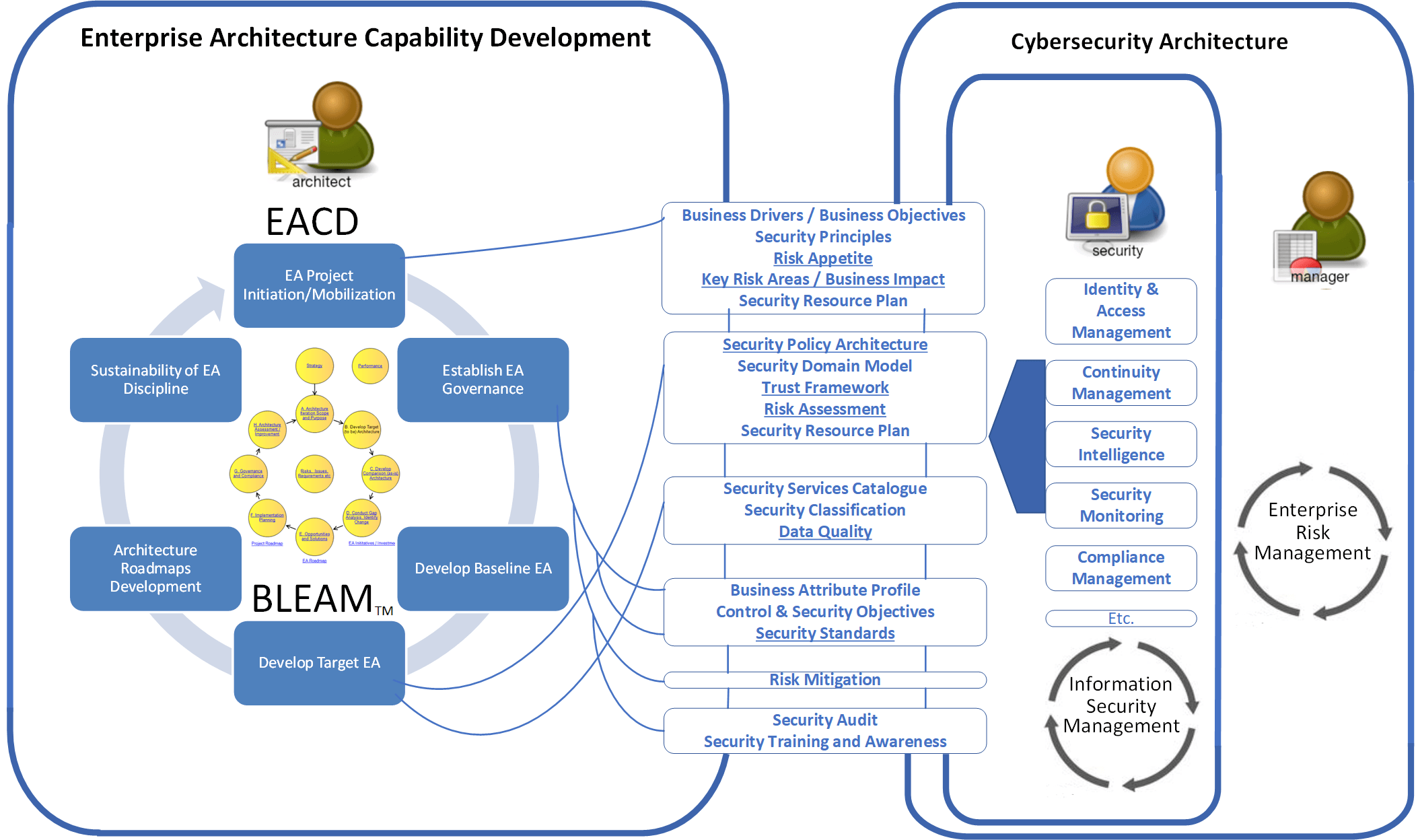
Cybersecurity framework helps safeguard your cyber environment These cybersecurity examples are just a sampling of the threats and defense steps out there today. An effective cyber security executive summary includes several essential sections. Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption. This course serves as an excellent primer to the many different domains of cyber security. Cyber security refers to.

What are Cyber Threats? Types, Levels and Examples Marketing91 Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption. While using w3schools, you agree to have read and accepted our. Posted at 00:16h in cyber security by stefan schulz. These cybersecurity examples are just a sampling of the threats and defense steps out there today. Piggybacking is a social engineering attack in which an.
Understanding these basics is the first step to. What are Cyber Threats? Types, Levels and Examples Marketing91.
This type of attack is often seen in office buildings, where an attacker will follow someone with an access. Deep learning methods such as lstm have been successfully applied to cyber security issues. The massive french insurance and financial services company axa it relies on the cybersecurity firm darktrace to deal with online threats. The famous capital one breach provides an example, as it resulted from problems with capital one’s cloud migration plan. Also, to make their computer systems safe from cyber threats. Security patches help prevent threat actor exploitation of security gaps and vulnerabilities, mitigating occurrences of threat attacks.
Understanding these basics is the first step to. This course serves as an excellent primer to the many different domains of cyber security. This type of attack is often seen in office buildings, where an attacker will follow someone with an access. What are Cyber Threats? Types, Levels and Examples Marketing91, But nowadays big companies, governments also use cybersecurity frameworks.







