It aims to gauge the strength of your company’s cyber security programs. What is a cyber security questionnaire?
Cybersecurity Example, Cyber security threats on the state level. Learning by reading we have created 16 tutorial pages for you to.

Maintain regression test suites for all components. Cybersecurity is a field that requires constant vigilance to stay ahead of the. Organizations should do what they can to prevent a cloud breach. Examples of cyber risks include:

Cybersecurity Frameworks — Types, Strategies, Implementation and It not only prevents unauthorized access, but it has other benefits such as minimizing resource wastage. The risks & threats section includes resources that includes threats and risks like ransomware, spyware, phishing and website security. Lockheed martin cyber kill chain. Annually complete cybersecurity development training covering the latest owasp top ten guidelines. This page includes resources that provide overviews of.

Pin by Gena Mannone on cybersecurity poster examples Cyber security Skilled in implementing information security infrastructure and balancing security initiatives to external risks and business operations. Cybersecurity is the protection of computer systems from criminals trying to. Trained 112 employees on security processes and risk mitigation techniques. This company cyber security policy template is ready to be tailored to your company’s needs and should be considered a starting point for.

Sample Cyber Security Business Plan Google Slides & Ppt Template Cyber Here are 10 of the best cybersecurity practices for businesses, employees and consumers. Ad achieve cybersecurity maturity with crystal eye xdr. Establish and follow a team code review standard. Usually, this is one of the main parts of a vendor due diligence process. Moreover, restricting access to administrative accounts enhances security by preventing unauthorized users from making system changes.

Cybersecurity example 2 Drupal One of the most important cybersecurity best practices is to install anti. Cyber security essay example thesis statement of cyber security essay. For example, a ceo has more access compared to a department manager. Establish and follow a team code review standard. For example, a program that claims it will speed up your computer may actually be sending confidential information.

Cybersecurity in medical devices Part 2 Stakeholders Software in Ad achieve cybersecurity maturity with crystal eye xdr. Few of them, however, know about all the malicious actions they might experience right after the button is pushed. To cover all of its bases, an organization should develop a comprehensive plan that includes not only these five types of cybersecurity, but also the three components that play active roles in a.

Cyber Security Degrees Lockheed martin cyber kill chain. A cyber security questionnaire is an evaluation form. Our cybersecurity activities also are driven by. Cyber attackers are known to execute repeat ransomware attacks, often because a proper forensics investigation was never completed the first time around. Learning by reading we have created 16 tutorial pages for you to.

How to Implement a Successful Cybersecurity Plan Every country has a team that is always working to reduce or deals with cases of hacking of internet data. Cybersecurity is the protection of computer systems from criminals trying to. Let’s take a look at the big three cybersecurity models used to investigate intrusions: An effective cyber security executive summary includes several essential sections. Ad achieve cybersecurity maturity with.

A framework to help make sense of cybersecurity tools Network World Lockheed martin cyber kill chain. Policy brief & purpose our company cyber security policy outlines our guidelines and provisions for preserving the security of our data and technology infrastructure. This paper examines two notable events of cyber warfare and security in our current age (the stuxnet attack on centrifuges, and the petya ransomware affecting citizens and governmental agencies), as well.

UK Government publishes common cyber attacks report IT Governance Blog Organizations should do what they can to prevent a cloud breach. Cyber attackers are known to execute repeat ransomware attacks, often because a proper forensics investigation was never completed the first time around. Here’s an example of what a resume summary for a cyber security professional looks like: Let’s take a look at the big three cybersecurity models used to.

Are You Cyber Secured? Be Aware of Potential Cyber Attacks ECS Here’s an example of what a resume summary for a cyber security professional looks like: Trained 112 employees on security processes and risk mitigation techniques. What is a cyber security questionnaire? For example, an organization that stores pii in the cloud may be subject to a ransomware attack. The lockheed martin cyber kill chain;

Cybersecurity Threats The risk management section includes resources that describe the importance of managing risk and. Lockheed martin cyber kill chain. Request a free demo now. Cyber security engineer with 10+ years of experience in cyber security, information security, and it operations. Ad achieve cybersecurity maturity with crystal eye xdr.

Effectively communicating cyber security to your board Security Colony The lockheed martin cyber kill chain; Cybersecurity analyst, raats tech dec. To cover all of its bases, an organization should develop a comprehensive plan that includes not only these five types of cybersecurity, but also the three components that play active roles in a cybersecurity posture: Cybersecurity is the protection of computer systems from criminals trying to. There are practical.

Printable Cyber Security Business Plan Google Slides & Ppt Template Cyber attackers are known to execute repeat ransomware attacks, often because a proper forensics investigation was never completed the first time around. It not only prevents unauthorized access, but it has other benefits such as minimizing resource wastage. Trained 112 employees on security processes and risk mitigation techniques. Ad achieve cybersecurity maturity with crystal eye xdr. Examples of cyber risks.

Cybersecurity Creating the Plan TechNation A cyber security questionnaire is an evaluation form. The risks & threats section includes resources that includes threats and risks like ransomware, spyware, phishing and website security. For example, an organization that stores pii in the cloud may be subject to a ransomware attack. Ad achieve cybersecurity maturity with crystal eye xdr. This cyber security tutorial provides basic and advanced.

Multimedia Gallery Infographic showing how NSFsupported Few of them, however, know about all the malicious actions they might experience right after the button is pushed. Establish and follow a team code review standard. Lockheed martin cyber kill chain. Organizations should do what they can to prevent a cloud breach. One of the most important cybersecurity best practices is to install anti.

What Is Internal Audit’s Role in Cyber Security? “ransomware attacks are a great example of this. Cybersecurity analyst, raats tech dec. Introduction of cyber security essay. Established standard operating procedures for security network. To cover all of its bases, an organization should develop a comprehensive plan that includes not only these five types of cybersecurity, but also the three components that play active roles in a cybersecurity posture:

Different Types Of Cyber Attack You Should Be Aware Off “ransomware attacks are a great example of this. Trained 112 employees on security processes and risk mitigation techniques. Maintain regression test suites for all components. It not only prevents unauthorized access, but it has other benefits such as minimizing resource wastage. Learning by reading we have created 16 tutorial pages for you to.

Cyber Security and Information Security KPI Examples Moreover, restricting access to administrative accounts enhances security by preventing unauthorized users from making system changes. Maintain regression test suites for all components. For example, a ceo has more access compared to a department manager. Cyber attackers are known to execute repeat ransomware attacks, often because a proper forensics investigation was never completed the first time around. It aims to.

Cyber Security Awareness Training the new norm? DC Main body of cyber security. Every day millions of people turn on their computers, laptops and gadgets with an irresistible desire to send, receive, share, exchange, delete or produce any kind of information. To cover all of its bases, an organization should develop a comprehensive plan that includes not only these five types of cybersecurity, but also the three components.

What to expect for the future of cybersecurity Preferred Technology Organizations should do what they can to prevent a cloud breach. An effective cyber security executive summary includes several essential sections. Cyber risks are sometimes referred to as security threats. This paper examines two notable events of cyber warfare and security in our current age (the stuxnet attack on centrifuges, and the petya ransomware affecting citizens and governmental agencies), as.

The What And How Of Cyber Threats Daily Infographic This company cyber security policy template is ready to be tailored to your company’s needs and should be considered a starting point for setting up your employment policies. Main body of cyber security. Every country has a team that is always working to reduce or deals with cases of hacking of internet data. Request a free demo now. Policy brief.

Cybersecurity example 3 Drupal Few of them, however, know about all the malicious actions they might experience right after the button is pushed. Introduction of cyber security essay. Established standard operating procedures for security network. This paper examines two notable events of cyber warfare and security in our current age (the stuxnet attack on centrifuges, and the petya ransomware affecting citizens and governmental agencies),.

Cyber Threat through USB drives still persistent Cybersecurity Insiders Lockheed martin cyber kill chain. This paper examines two notable events of cyber warfare and security in our current age (the stuxnet attack on centrifuges, and the petya ransomware affecting citizens and governmental agencies), as well as examines how these attacks shape foreign and domestic policies and procedures. Cybersecurity is a field that requires constant vigilance to stay ahead of.

A Beginner�s Guide To Cybersecurity Framework Edureka Cyber attackers are known to execute repeat ransomware attacks, often because a proper forensics investigation was never completed the first time around. Cyber security essay example thesis statement of cyber security essay. To cover all of its bases, an organization should develop a comprehensive plan that includes not only these five types of cybersecurity, but also the three components that.
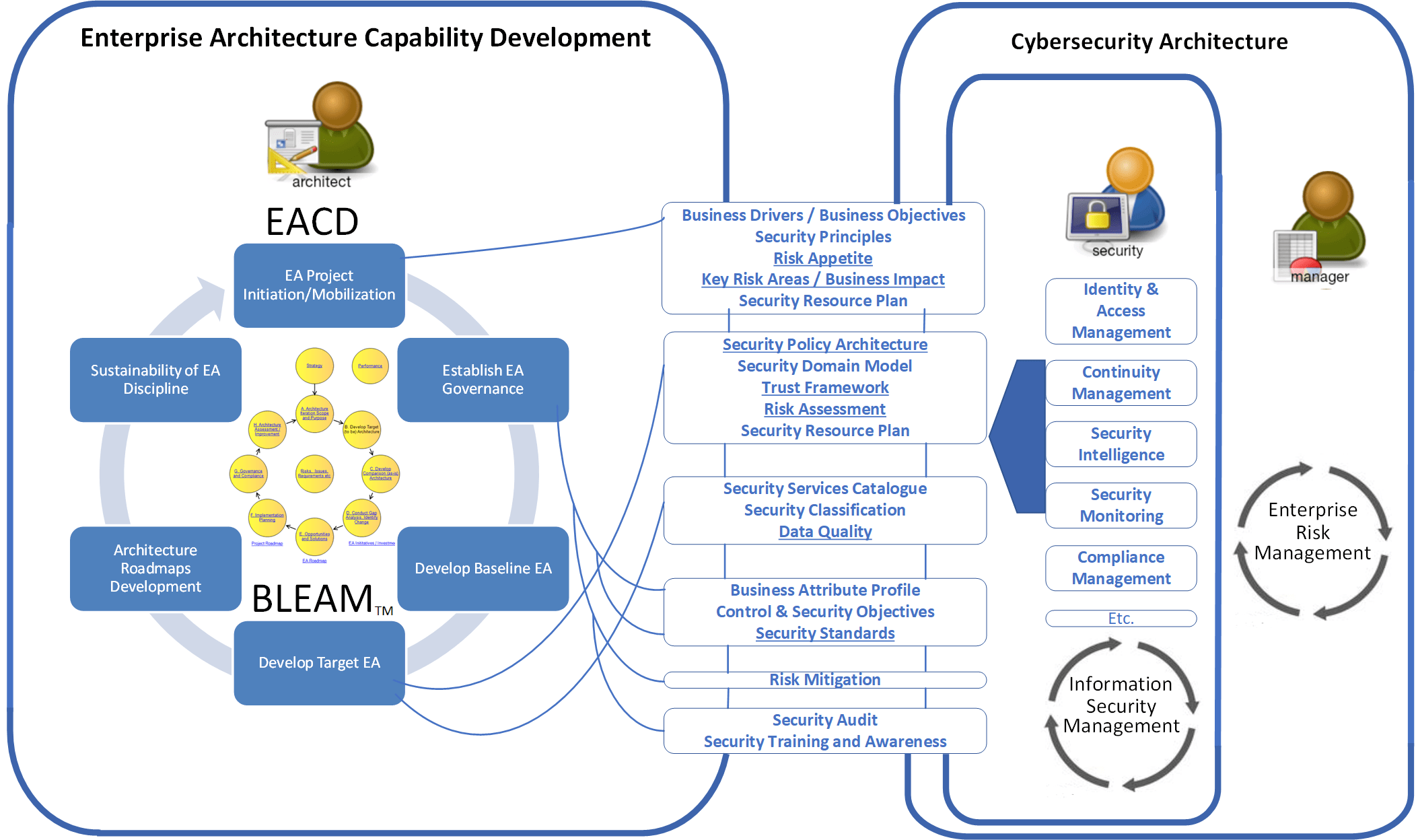
Cybersecurity framework helps safeguard your cyber environment Skilled in implementing information security infrastructure and balancing security initiatives to external risks and business operations. This company cyber security policy template is ready to be tailored to your company’s needs and should be considered a starting point for setting up your employment policies. Cyber attackers are known to execute repeat ransomware attacks, often because a proper forensics investigation was.
Request a free demo now. Cybersecurity framework helps safeguard your cyber environment.
For example, a ceo has more access compared to a department manager. Moreover, restricting access to administrative accounts enhances security by preventing unauthorized users from making system changes. Cyber attackers are known to execute repeat ransomware attacks, often because a proper forensics investigation was never completed the first time around. Cyber security threats on the state level. For example, a ceo has more access compared to a department manager. Cybersecurity analyst, raats tech dec.
Though commonly used interchangeably, cyber risks and vulnerabilities are not the same. Cyber security engineer with 10+ years of experience in cyber security, information security, and it operations. Every day millions of people turn on their computers, laptops and gadgets with an irresistible desire to send, receive, share, exchange, delete or produce any kind of information. Cybersecurity framework helps safeguard your cyber environment, This course serves as an excellent primer to the many different domains of cyber security.







