Some fundamental but vital practices can help companies avoid cybercrimes or attacks.”. Department for digital, culture, media & sport
Cyber Essentials Meaning, Which network equipment for homeworkers can be included from the scope; Quizzes allow for partial credit scoring on all item types to foster […]continue.

A cloud service, for cyber essentials purposes, is defined as a subscription (paid or free) service where the applicant controls who has access and/or administrative access over the cloud service. The practice is used by individuals and enterprises to protect against unauthorized access to data centers and other computerized systems. Simply being certified can reduce your cyber risk by up to 98.5%. Learn about threats to computer systems and ways to secure their computers.

Cyber Essentials Citrus IT Support Many government bodies require cyber essentials certification from any supplier or service provider they work with. For example ms 365, google workspace, quickbooks, dropbox etc. It provides a cyber security certification scheme that was developed as a part of the uk government’s national cyber security strategy. Also, administration privileges are only. As part of our commitment to cybersecurity, buckinghamshire business.

What is a Ransomware Attack? How to prevent it? However you define your boundary, the cyber essentials requirements will apply to any devices within the scope that meet one of the following conditions: Get onboard—and develop an understanding of cybercrime, security principles, technologies, and procedures used to defend networks. These cia security objectives are essential in keeping information and systems secure. Cyber essentials provides security benefits which significantly. Also,.

IASME Wins Cyber Essentials Partnership What Does This Mean? Cia stands for confidentiality, integrity and availability in cyber security and collectively form important security objectives for many organizations to protect information. So getting certified could open up new avenues for your business. Iasme allowing a grace period before cracking down on: It is designed to test the skills and knowledge presented in the course. In the simplest case, this.

Why Cybercrime is increasing Cyberfort Knowledge It is designed to test the skills and knowledge presented in the course. For example ms 365, google workspace, quickbooks, dropbox etc. Also known as information technology (it) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization. Learn about threats to computer systems and ways.

Cybersecurity tips which you should practice more often The Frisky Quizzes allow for partial credit scoring on all item types to foster […]continue. Download the cyber essentials starter kit, the basics for building a culture of cyber readiness. Department for digital, culture, media & sport Cyber essentials questionnaire guidance introduction this document has been produced to help companies write a response to each of the questions and therefore provide a.

We�ve achieved Cyber Essentials Plus Certification! The practice is used by individuals and enterprises to protect against unauthorized access to data centers and other computerized systems. Iasme allowing a grace period before cracking down on: Cyber essentials covers everything your business should do to protect itself from cyberattacks. Which network equipment for homeworkers can be included from the scope; Launched in 2014, the government’s cyber essentials.

The Definitive Cyber Security Guide for Small to Medium Businesses Certification to the scheme will demonstrate to your customers and business partners that fundamental cyber security measures are in place, and provides evidence of your. Which network equipment for homeworkers can be included from the scope; The ncsc’s (national cyber security centre) guidance on firewalls can be found as part of their cyber security scheme “10 steps”. A strong cybersecurity.

Cyber Security Essential 8 What Does it Mean for Your Business Cybersecurity essentials 1.1 final quiz answers 100% 2018 quiz instructions this quiz covers all of the content in cybersecurity essentials 1.1. Which network equipment for homeworkers can be included from the scope; A cloud service, for cyber essentials purposes, is defined as a subscription (paid or free) service where the applicant controls who has access and/or administrative access over the.
![[Withdrawn] Common Cyber Attacks Summary GOV.UK [Withdrawn] Common Cyber Attacks Summary GOV.UK](https://i2.wp.com/assets.publishing.service.gov.uk/government/uploads/system/uploads/image_data/file/35290/common_cyber_attacks.png)
[Withdrawn] Common Cyber Attacks Summary GOV.UK Department for digital, culture, media & sport Certification to the scheme will demonstrate to your customers and business partners that fundamental cyber security measures are in place, and provides evidence of your. The ncsc’s (national cyber security centre) guidance on firewalls can be found as part of their cyber security scheme “10 steps”. The key here is that they need.

3d Image Cyber Stalking Issues Concept Word Cloud Background Stock Cyber essentials covers everything your business should do to protect itself from cyberattacks. Please note that it is just a guide to help you understand what goes through an assessors mind when reading through responses. Also known as information technology (it) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside.

Cyber Essentials What Does it Mean, and Why Does it Matter? Prism A cloud service, for cyber essentials purposes, is defined as a subscription (paid or free) service where the applicant controls who has access and/or administrative access over the cloud service. Please note that it is just a guide to help you understand what goes through an assessors mind when reading through responses. This effectively creates a ‘buffer zone’ between your.

What is Cyber Essentials? Requirements for it infrastructure by implementing restrictions, known as ‘firewall rules’, which can allow or block traffic according to its source, destination and type of. Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. This effectively creates a ‘buffer zone’ between your it network or device and other, external networks. An essential part of cyber.

About Us East Anglian Air Ambulance The key here is that they need to be a necessity to your organisation. That is why the demand for security professionals continues to grow. “there are several types of cyberattacks, but a significant number are very basic, carried out by amateurs. Cisa’s cyber essentials is a guide for leaders of small businesses as well as leaders of small and.

Core cybersecurity principles for new companies and products Help Net The key here is that they need to be a necessity to your organisation. However you define your boundary, the cyber essentials requirements will apply to any devices within the scope that meet one of the following conditions: Cybersecurity essentials 1.1 final quiz answers 100% 2018 quiz instructions this quiz covers all of the content in cybersecurity essentials 1.1. A.
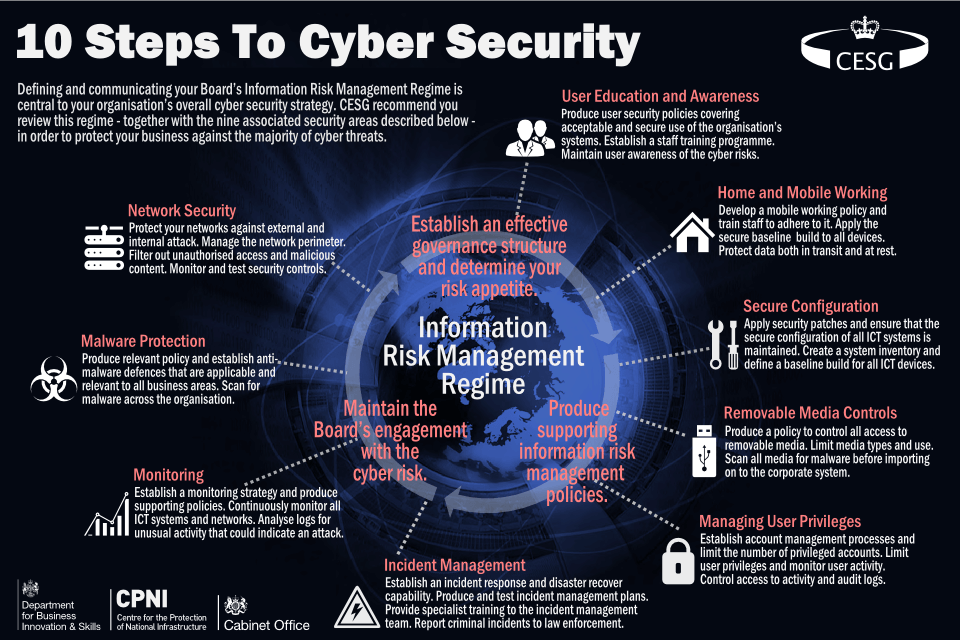
EMSS Cyber security guidance for business Very helpful information Cyber essentials provides security benefits which significantly. A single breach can have huge consequences for a company, hurting the bottom line and causing disruption in the daily lives of millions of people. So getting certified could open up new avenues for your business. Many government bodies require cyber essentials certification from any supplier or service provider they work with. It.

Cyber Essentials Plus IT Security Accreditation for Glasgow & Edinburgh Download the cyber essentials starter kit, the basics for building a culture of cyber readiness. In the simplest case, this means between your computer (or computers) and ‘the internet’. Please note that it is just a guide to help you understand what goes through an assessors mind when reading through responses. Simply being certified can reduce your cyber risk by.

a Paralegal Working in and Cyberspace Law As a cyber essentials scheme applicant, you will need to ensure that your organisation meets all the requirements of the scheme. The key here is that they need to be a necessity to your organisation. Some fundamental but vital practices can help companies avoid cybercrimes or attacks.”. Quizzes allow for partial credit scoring on all item types to foster […]continue..
![[Withdrawn] 10 Steps Executive Companion GOV.UK [Withdrawn] 10 Steps Executive Companion GOV.UK](https://i2.wp.com/assets.publishing.service.gov.uk/government/uploads/system/uploads/image_data/file/35243/10_steps_portrait_red_headings.png)
[Withdrawn] 10 Steps Executive Companion GOV.UK Which network equipment for homeworkers can be included from the scope; Cloud services and thin clients are now required to be in scope; The ict cybersecurity essentials course focuses on fundamentals of personal online security and safety. That is why the demand for security professionals continues to grow. As part of our commitment to cybersecurity, buckinghamshire business first achieved cyber.

Cyber Essentials Plus Get A Little Help However you define your boundary, the cyber essentials requirements will apply to any devices within the scope that meet one of the following conditions: This effectively creates a ‘buffer zone’ between your it network or device and other, external networks. Which network equipment for homeworkers can be included from the scope; The practice is used by individuals and enterprises to.

What is Cyber Security? Definition, Types, and User Protection Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. Cyber essentials questionnaire guidance introduction this document has been produced to help companies write a response to each of the questions and therefore provide a good commentary for the controls in use. The practice is used by individuals and enterprises to protect against unauthorized access to.

How To Get The Cyber Essentials Logos On Your Organisation�s Website This accreditation demonstrates to suppliers, members and employees alike that we can be trusted with their data and have robust cyber security practices in place. A single breach can have huge consequences for a company, hurting the bottom line and causing disruption in the daily lives of millions of people. You will receive a cyber essentials logo for your website,.

System Force Achieves CREST Cyber Essentials System Force I.T. Cyber essentials questionnaire guidance introduction this document has been produced to help companies write a response to each of the questions and therefore provide a good commentary for the controls in use. Cisa’s cyber essentials is a guide for leaders of small businesses as well as leaders of small and local government agencies to develop an actionable understanding of where.

What is Cyber Security? Definition & Best Practices Download the cyber essentials starter kit, the basics for building a culture of cyber readiness. Iasme allowing a grace period before cracking down on: Cyber essentials questionnaire guidance introduction this document has been produced to help companies write a response to each of the questions and therefore provide a good commentary for the controls in use. Quizzes allow for partial.

RTITB Achieves Cyber Essentials Certificate of Assurance RTITB Many government bodies require cyber essentials certification from any supplier or service provider they work with. This accreditation demonstrates to suppliers, members and employees alike that we can be trusted with their data and have robust cyber security practices in place. Launched in 2014, the government’s cyber essentials scheme aims to help organisations better manage the variety of business issues.

Cyberbullying in Social Media within Educational Institutions Requirements for it infrastructure by implementing restrictions, known as ‘firewall rules’, which can allow or block traffic according to its source, destination and type of. For example ms 365, google workspace, quickbooks, dropbox etc. Cia stands for confidentiality, integrity and availability in cyber security and collectively form important security objectives for many organizations to protect information. Certification to the scheme.
Which network equipment for homeworkers can be included from the scope; Cyberbullying in Social Media within Educational Institutions.
There are multiple task types that may be available in this quiz. Many government bodies require cyber essentials certification from any supplier or service provider they work with. Certification to the scheme will demonstrate to your customers and business partners that fundamental cyber security measures are in place, and provides evidence of your. Cybersecurity essentials 1.1 final quiz answers 100% 2018 quiz instructions this quiz covers all of the content in cybersecurity essentials 1.1. So getting certified could open up new avenues for your business. You will receive a cyber essentials logo for your website, which helps to give stakeholders peace of mind when dealing with you.
This accreditation demonstrates to suppliers, members and employees alike that we can be trusted with their data and have robust cyber security practices in place. Cyber essentials questionnaire guidance introduction this document has been produced to help companies write a response to each of the questions and therefore provide a good commentary for the controls in use. As a cyber essentials scheme applicant, you will need to ensure that your organisation meets all the requirements of the scheme. Cyberbullying in Social Media within Educational Institutions, Cisa’s cyber essentials is a guide for leaders of small businesses as well as leaders of small and local government agencies to develop an actionable understanding of where to start implementing organizational cybersecurity practices.







